Key Findings:
- Microsoft security scams trick the user into thinking they’re locked out of their computer.
- 70% of victims visited these scam sites because they clicked on a malicious Google search result.
- Majority of the websites were hosted on cloud service provider hosting domains.
Overview
Keep Aware’s Threat Research division identified a recent batch of fraudulent Microsoft support sites. While these scam campaigns are not novel, they persist as an online security risk for all internet users. The scam sites impersonate Microsoft, deceive the user into thinking their machine is infected, and prompt the user to call them via a phone number they claim is Microsoft’s. This type of scam is often socially engineering victims into supplying personal information, divulging financial data, transferring money, or providing direct access to their device.
Majority of these sites were visited by clicking on malicious Google search results. Most Microsoft scam sites employ a combination of behaviors, such as auto fullscreen and using audio, to further deceive a victim. Additionally, most of the recent websites observed are on cloud hosting platforms, specifically Amazon S3 and CloudFront, Microsoft Azure, and Digital Ocean.
Initial Access: Searching for Social Media Logins
Approximately 70% of these scam site visits occurred because a user clicked on a malicious Google search result. Interestingly, users were specifically searching for logins to Facebook and Youtube. At this time, it’s unclear whether they were a result of malvertising via search engine ads or of SEO poisoning.
Microsoft Security Scam Sites: Commonalities
These recent Microsoft security scams have overlapping characteristics, including:
- They impersonate Microsoft or Microsoft Windows Defender;
- They claim the victim’s access to the computer is locked/blocked for security reasons;
- The website is often just an image or a GIF;
- Their call to action prompts the user to call a “Microsoft” support number.
Majority of the Microsoft security scams identified are hosted on cloud service provider hosting platforms, such as Amazon S3 or Microsoft Azure domains; the remaining domains were young (i.e., registered less than a year ago).
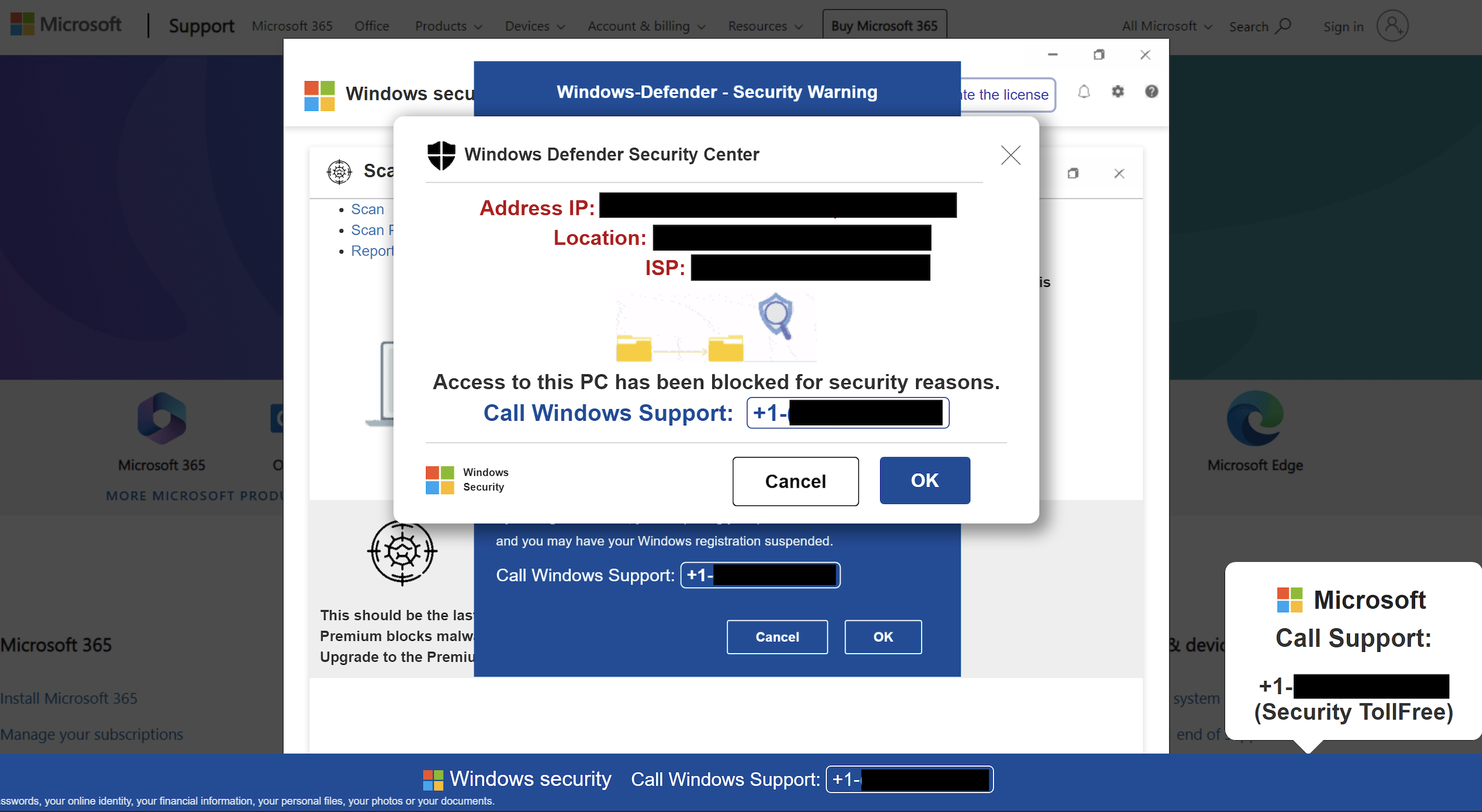
Though most of the scam websites have since been taken down, see the below screenshots for a couple examples:
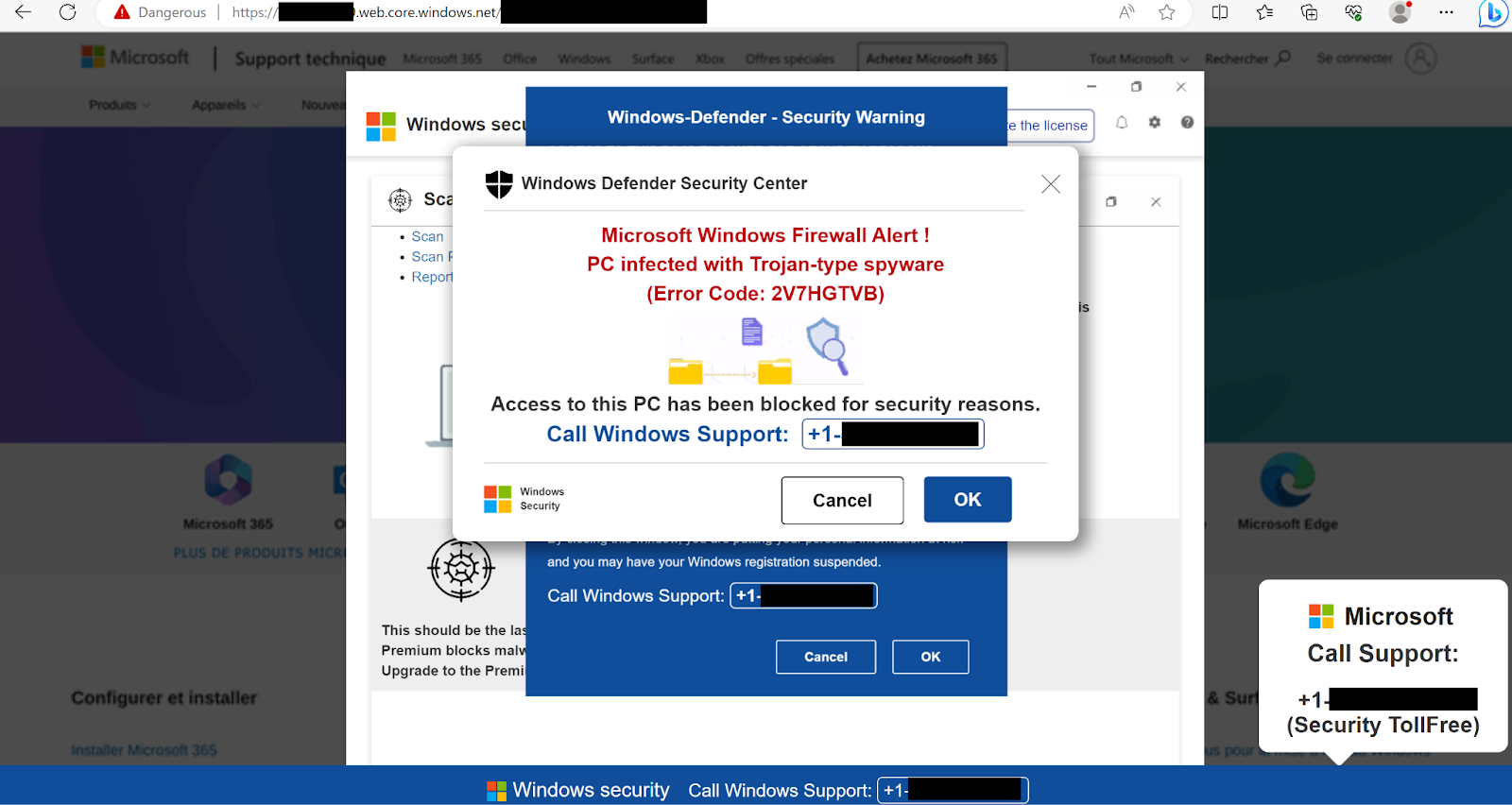
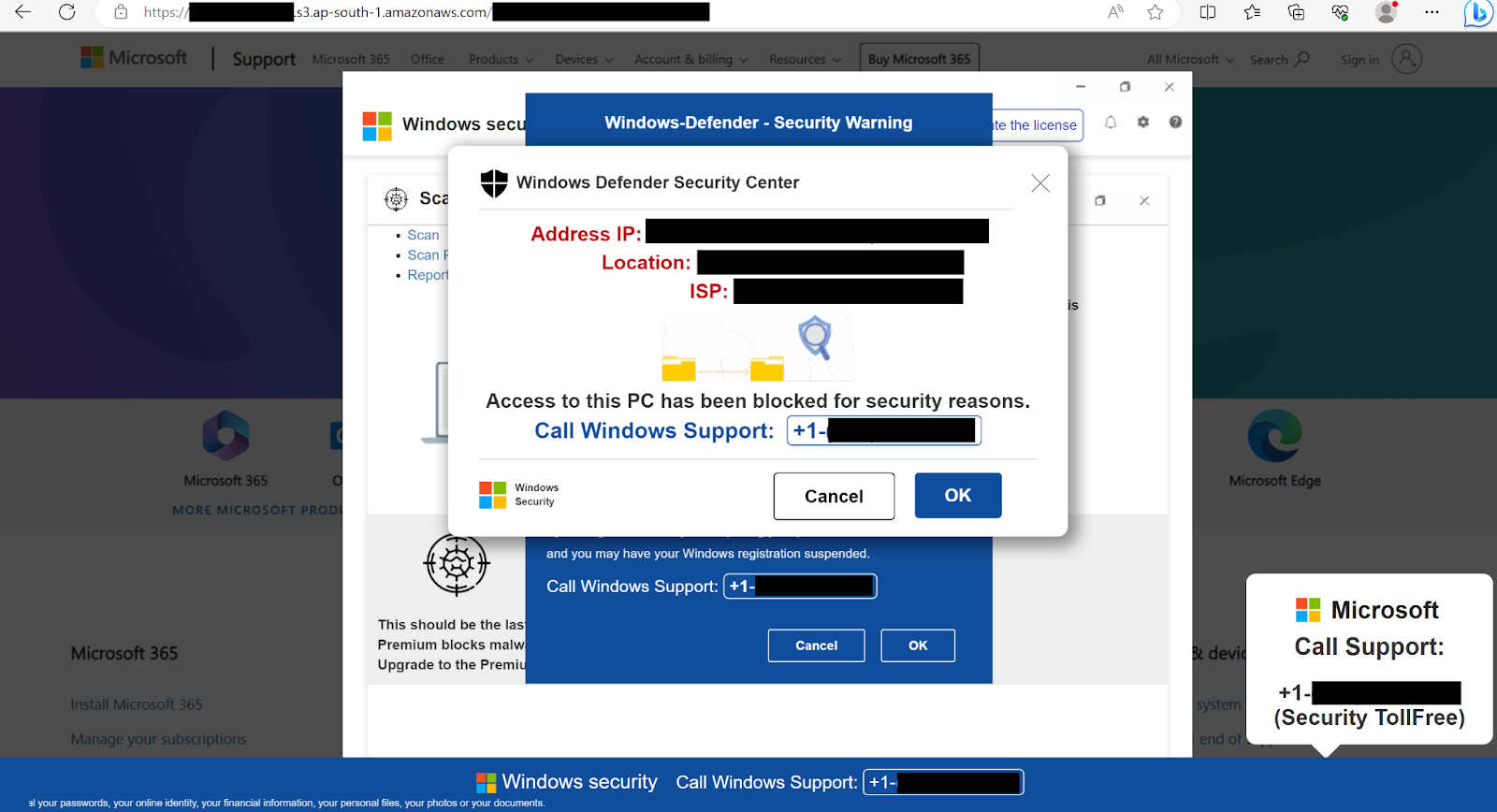
As seen in the above images, these Microsoft security scam sites make it appear as if there is a website popup or a desktop notification; however, they are just an image or a GIF on the webpage. When the user tries to click on a “button” to cancel, accept, or close the (fake) popups, the website does not respond; thus, the user believes the alert that they have been locked out of accessing their computer.
Prevalent Behaviors
In addition to above common looks, all Microsoft scam sites observed have a combination of the following behaviors:
- Making the webpage fullscreen;
- Disabling keyboard shortcuts;
- Playing audio that states the device is infected;
- Looking up IP information;
- Tracking web traffic using Google analytics.
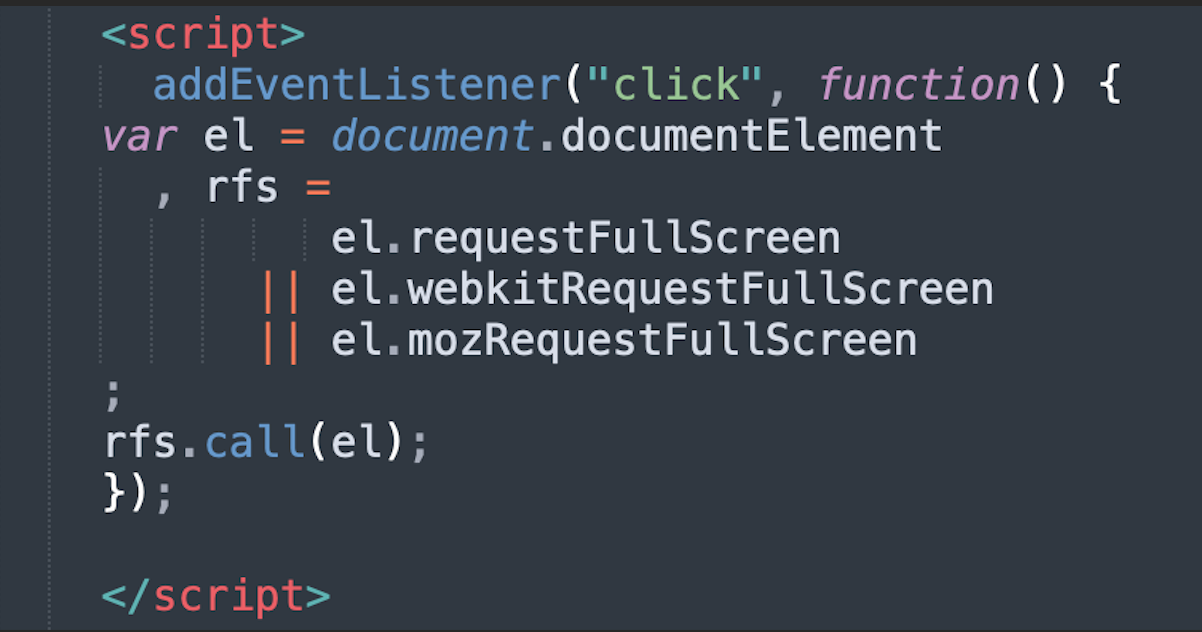
Making the Webpage Fullscreen.
Many of these malintent websites will add JavaScript code, such as below, to make the webpage fullscreen once the user clicks anywhere. If the user is not technologically-savvy and knows to use “Esc” or other keyboard commands to exit fullscreen, they may fall victim into further believing they have been locked out of accessing their device.
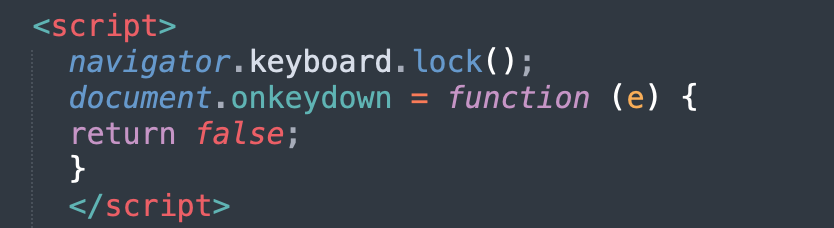
Disabling Keyboard Shortcuts.
Even if the user does know to use certain keyboard shortcuts, such as “Esc” to escape the fullscreen mode, many of these sites will also disable certain keys, as illustrated by the below code screenshots, which were taken from different Microsoft scam sites. Disabling these keys further reinforces victim’s belief that they have indeed been denied access to their computer.
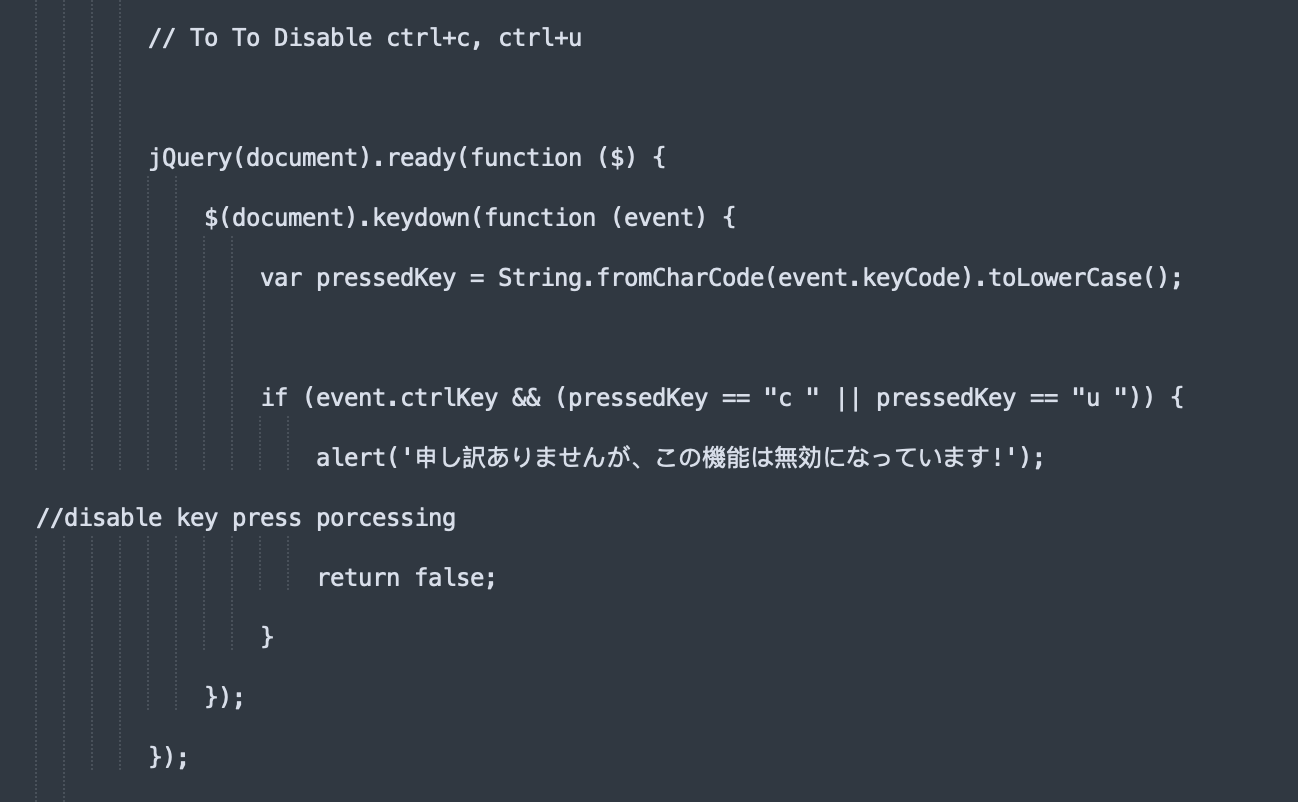
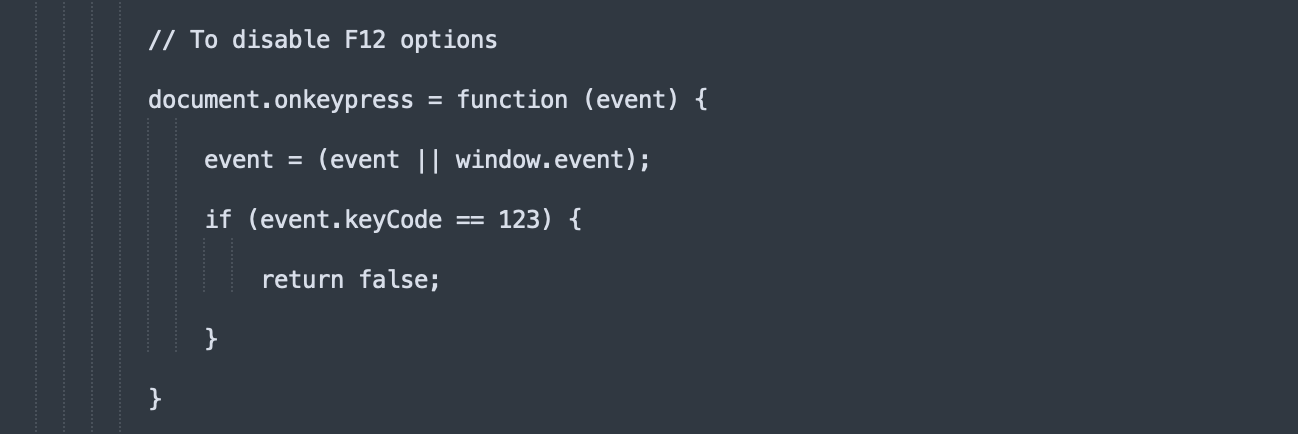
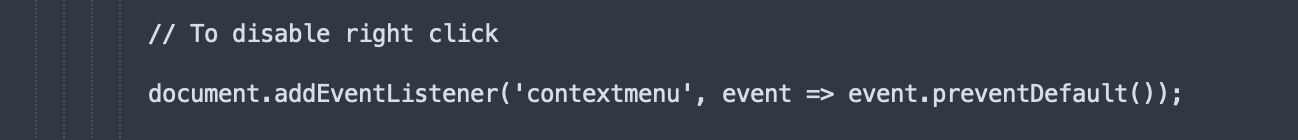
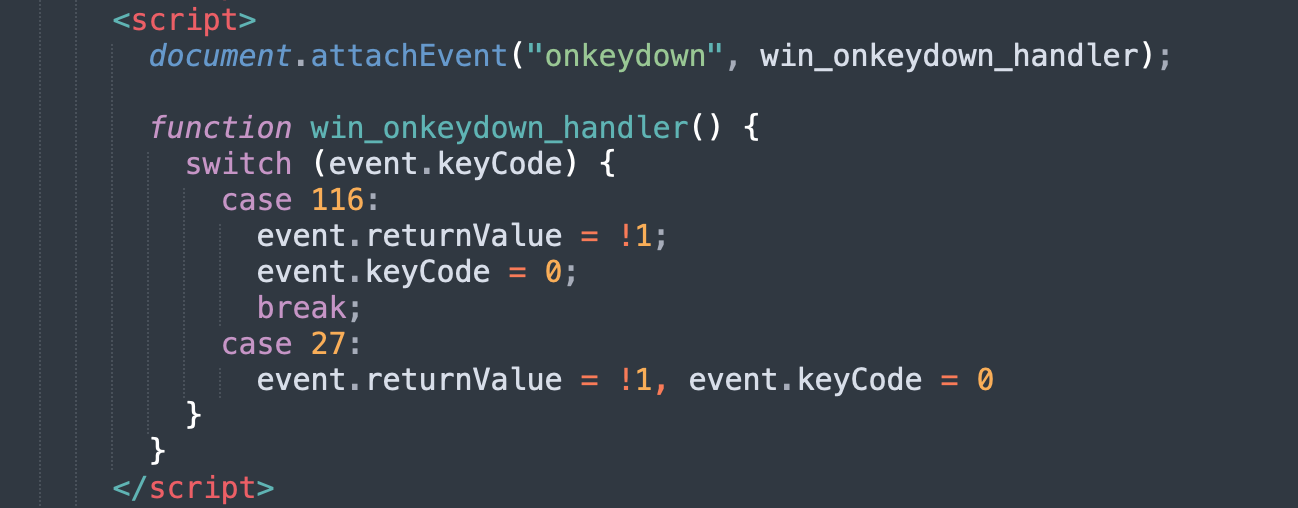
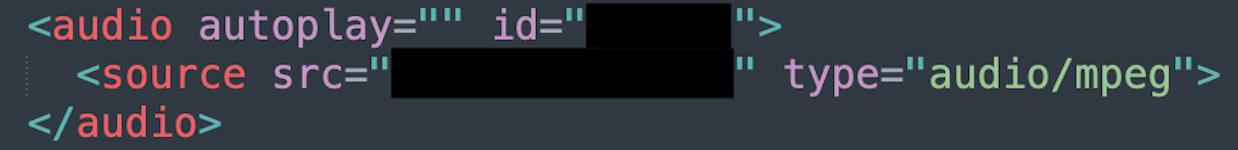
Playing Audio that States the Device is Infected.
Most of these malicious websites will also play an audio file that states their machine is locked for security reasons and to promptly call their support number. These audio files might play after a user performs a particular action, such as clicking on the webpage, or automatically.
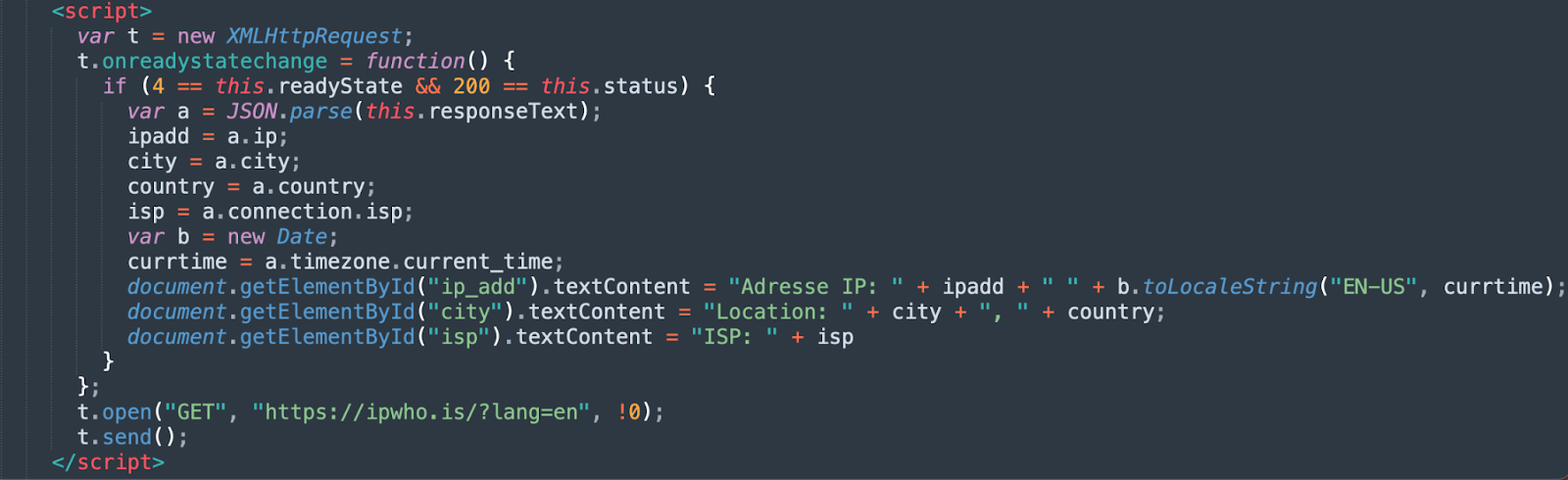
Looking Up IP Information.
Additionally, the websites might make web requests to gather and then display IP information, such as the user’s IP address, the IP’s ASN, and the city. The attacker’s website then displays this information. Often accompanied with an audio message saying something like, “… Your IP address was used without your knowledge or consent to visit websites that contains identity-theft virus. …”, further attempting to dupe the victim into believing their device is compromised.
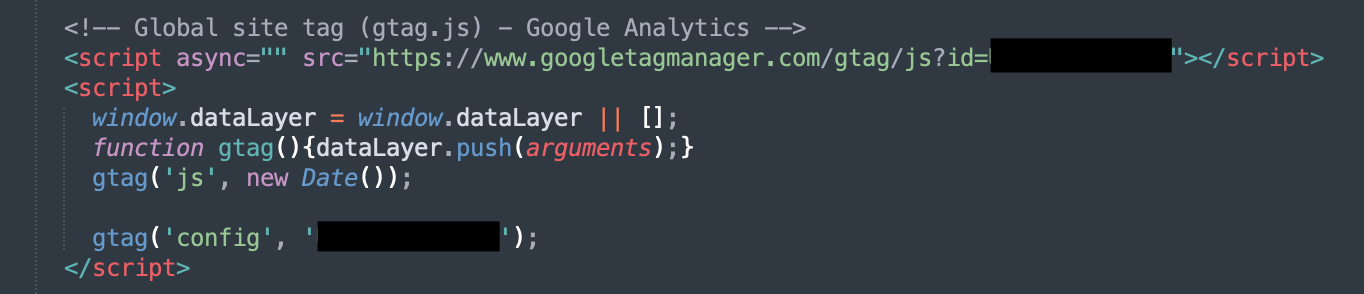
Tracking Web Traffic Using Google Analytics.
Another prevalent behavior is tracking web traffic via Google Analytics.
Recommendations: Risk Reduction
To limit the likelihood of employees being exposed to this and other campaigns, consider blocking traffic to young domains and to cloud service hosting domains and allowlisting traffic only to cloud service hosting subdomains that your organization uses for business purposes.
Additionally, to reduce the impact when an employee inadvertently goes to a Microsoft scam site, ensure that browser-based social engineering attacks are included in your organization’s cybersecurity awareness program for employees.
Conclusion
Though Microsoft support impersonation sites first appeared many years ago, they remain an ongoing threat. They socially engineer the victim into calling the scammers by deceiving the user into believing they have been locked out of controlling their computer, and these scam sites are now often hosted on cloud service provider domains.
Lead Threat Researcher
Erin Kuffel
IOCs
Domains and URLs
| Domain | URL(s) |
| d14xnavda0b9mk[.]cloudfront[.]net | https[:]//d14xnavda0b9mk[.]cloudfront[.]net/ |
| ghbhhyyu[.]z13[.]web[.]core[.]windows[.]net | https[:]//ghbhhyyu[.]z13[.]web[.]core[.]windows[.]net/Win08SuDeEr086/index[.]html |
| sharma12[.]z9[.]web[.]core[.]windows[.]net | https[:]//sharma12[.]z9[.]web[.]core[.]windows[.]net/Win08ShDMeEr0887/index[.]html |
| lionfish-app-whz47[.]ondigitalocean[.]app | https[:]//lionfish-app-whz47[.]ondigitalocean[.]app/Win08SuDeEr086/index[.]html |
| sea-turtle-app-u2aph[.]ondigitalocean[.]app | https[:]//sea-turtle-app-u2aph[.]ondigitalocean[.]app/Win08SuDeEr086/index[.]html |
| win08d73bdc0de7[.]s3[.]ap-northeast-1[.]amazonaws[.]com | https[:]//win08d73bdc0de7[.]s3[.]ap-northeast-1[.]amazonaws[.]com/win08d73bdc0de7[.]html |
| terebinajeenafb3[.]s3[.]ap-south-1[.]amazonaws[.]com | https[:]//terebinajeenafb3[.]s3[.]ap-south-1[.]amazonaws[.]com/Win08SmtDaEr08d8d77/index[.]html |
| brainboostiq[.]org | https[:]//brainboostiq[.]org/ |
| dreamelv[.]shop | https[:]//dreamelv[.]shop/Win08ShDMeEr0887/index[.]html |
| tenkisano[.]click | https[:]//tenkisano[.]click/Win08WekyMeEr0887/index[.]html |