Key Topics and Findings:
- Security support scams employ a variety of social engineering techniques to spur panic.
- Approximately 1 in 4 events occurred because a user clicked on a malicious search engine result.
- 76% of security scam sites were hosted on cloud service provider domains.
- Risks to employers are amplified when an employee falls victim to this browser-initiated attack while using a company device.
- A call for both human- and technical-based approaches to mitigating risk.
Overview
In today’s interconnected world where practically all employees use the internet, the prevalence of security support scams and other social engineering sites remains a concern. In a threat post specifically about Microsoft security scam websites, our Threat Research team discussed recent web pages impersonating Microsoft that are falsely claiming a user’s device has been infected.
This article provides a comprehensive examination of security scam websites. It aims to shed light on the social engineering techniques employed by these scams, their impact on employees and organizations, the methods through which victims are lured to these deceptive sites, and the hosting means of such fraudulent websites.
Security Support Scams: Spur Panic, then Propose Support
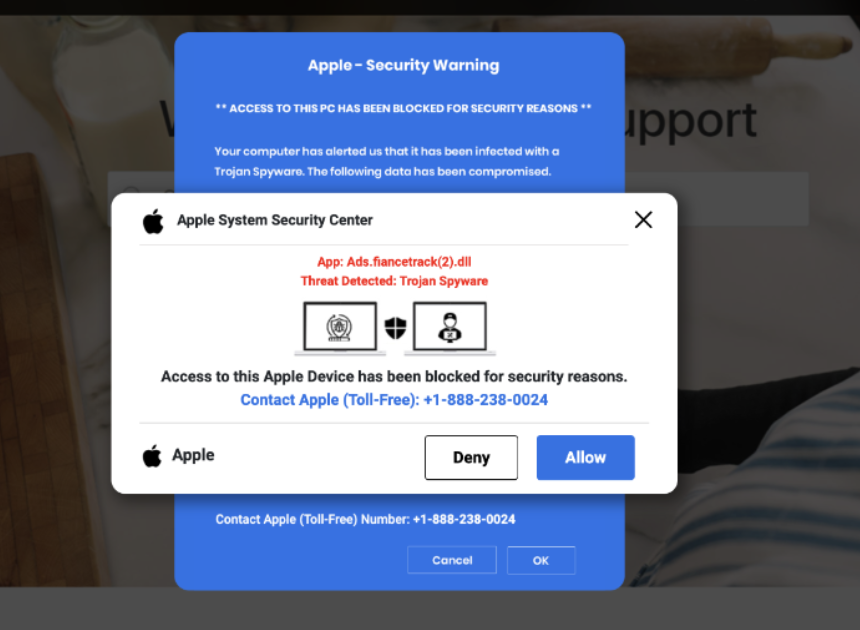
Security support scam sites often impersonate a well-known brand, such as Microsoft or Apple. The websites will look like there are popups or desktop notifications from a security product (e.g., Windows Defender) falsely proclaiming the user’s device is infected.
However, the “notifications” are often just an image or a GIF on the website; thus, when the user tries to click on a “button” to cancel, accept, or close these (fake) popups, the website does not respond, and the user then believes the alert that they have been locked out of accessing their computer.
For the more interactive pages, pressing an “OK” or “Cancel” button, for example, might make that warning disappear – until the mouse moves again; at which point, that same warning message will reappear.
Below are some common behaviors these pages employ to deceive users:
- Making the webpage fullscreen to make the victim believe they have been locked out of their computer;
- Disabling the keyboard or certain keys to reinforce the notion that their machine is locked;
- Playing audio that states their device is infected to further dupe the user into thinking their device is compromised;
- Displaying IP information, which can create a sense of validity to the fraudulent claim.
Additionally, these types of scam sites will often play an audio file that is meant to spur even more panic into the victim.
For more coverage of common behaviors and code examples, see our threat post about recent Microsoft security support scam sites.
These social engineering tactics, especially when used in tandem, trigger a victim to feel panic; and the attacker’s site offers “support” to help the panicked victim through their “security issue” – all they have to do is give the scammer a call.
The End Game: Money
The primary goal of many scams is gaining money, and it appears to be no different for security scam sites. The scams will likely ask for sensitive information (e.g., credit card details or credentials to accounts) but are ultimately motivated by financial gain.
How do the scammers attempt to get money once a victim calls them? Common schemes include:
- Sell unnecessary security software.
- Directly ask for payment to “fix” the problem.
- Request sensitive information, such as credit card details or bank information.
- Gain remote access and then install either ransomware (and demand ransom) or other malware (such as keyloggers to log credentials).
Having explored the tactics employed by these scammers and their financial motive, let’s cover how Keep Aware has observed victims end up browsing to these scam websites.
Initial Access: Older Domains and Malicious Search Results
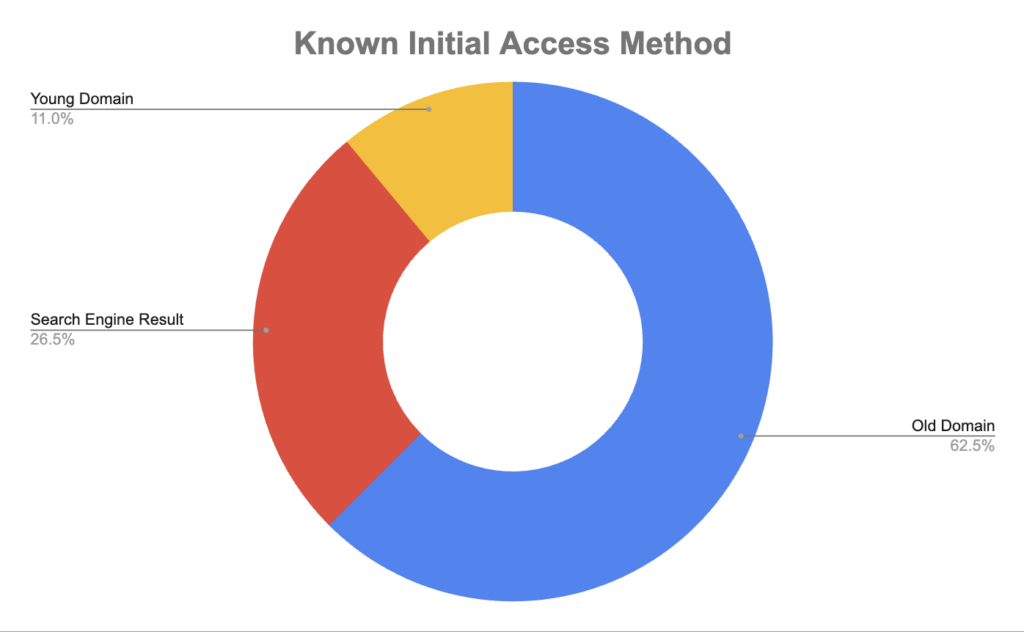
Over a 6-month timeframe, over half of the security scam site visits were traced back to domains registered more than one year prior to the event. These older domains were either serving ads, redirecting, or embedding links to malicious sites.
Approximately 1 in 4 events occurred because a user clicked on a malicious search engine result. What were users searching for? The top 3 buckets of searched terms, in decreasing order, were for:
- Facebook,
- Amazon Prime, and
- Youtube.
These buckets each included variations and misspellings of the term (e.g., “facebook login” or “faecbook”; “amazon prime login” or “amzon prime”).
Just Block Young Domains? Think Again.
To prevent employees from encountering this type of scam campaign, many IT and security departments consider blocking traffic to young domains – commonly defined as domains registered less than a year ago – because the assumption is that these scam sites are often hosted on young domains.
Although this defense tactic can protect your organization from many phishing, scam, and other malicious sites, our data from recent security support scams shows there is more to consider. Specifically, the majority of the scam sites were actually hosted on cloud provider hosting platforms.
As illustrated by the above chart, under 20% of these recent scam sites were hosted on a young domain. Of note, our data shows some domains were created the day of the respective incident.
A small percentage of the sites were either accessed directly using an IP address or hosted on an older, non-cloud provider domain.
The remaining 76% of security scam sites were hosted on cloud service provider domains (i.e., domains registered years ago and by trusted third parties, such as Microsoft). In other words, just blocking young domains will help – but certainly won’t prevent – this browsing threat.
The Role of Cloud Provider Hosting: Bypass Traditional Security Controls
Majority of the recent scam websites identified were hosted on cloud service provider hosting platforms, such as Amazon S3 or Microsoft Azure domains. Below are both the specific cloud hosting domains identified as part of the campaigns and an example full URL of a scam website.
| Cloud Hosting Platform | Domain Observed |
| Amazon Amplify | amplifyapp.com |
| Amazon Cloudfront | cloudfront.net |
| Amazon S3 | s3.<region>.amazonaws.com |
| Digital Ocean | ondigitalocean.app |
| Google Cloud Run | run.app |
| Microsoft Azure | web.core.windows.net |
| https[:]//ninju12[.]z9[.]web[.]core[.]windows[.]net/Win08ShDMeEr0887/index[.]html |
Why are scammers opting to use cloud hosting platforms? We suspect the listed objectives are prominent reasons:
- For reliable uptime.
- For anonymity and ease of setup.
- To abuse a victim’s trust in cloud providers.
- To bypass young domain blocking rules.
Scammers, phishers, and other actors with malintent are abusing – and will continue to abuse – your organization’s trust through older domains registered by a known and often trusted third party, such as Microsoft. As part of a cybersecurity defense-in-depth approach, consider blocking cloud service hosting domains and allowlisting only the subdomains your organization legitimately uses for business purposes.
Scam Risks: Why both Employees and Employers Should Care
When an employee falls victim to these sorts of scams, both the employee and the employer could be affected. On a personal level, IT and security support scams can pose risks of privacy invasion, financial loss, unintended data exposure, and unauthorized device access.
Businesses, in turn, may face possible leakage of sensitive company data, financial loss, and subsequent security breaches. These risks to employers are amplified when the employee falls victim to this browser-initiated attack while using a company device. The table below lists a small subset of risks to the user and to the organization.
| Risks to User | Risks to Organization |
| Financial loss. | Financial loss. |
| Disclosure of sensitive personal information (e.g., SSN, banking information). | Disclosure of sensitive information (e.g., banking information). |
| Mental energy is focused on the perceived and actual consequences of this scam. | Loss of productivity. |
| Remote control of device. Further damage to the local machine and to personal data. | Remote control of device. Attacker has access to company data stored on the victim’s machine. Attacker has gained initial access and can scan and move laterally in the enterprise network / cloud resources. |
Security Best Practices: Two-Pronged Risk Reduction
Given the potential impacts of employees falling victim to IT security support scams, there is a crucial need for browser-based social engineering attacks to be included in comprehensive cybersecurity awareness programs for employees. Simultaneously, IT security teams can implement proactive measures, such as blocking traffic to suspicious domains, young domains, and cloud service hosting domains not used by your organization.
By taking these steps in tandem, both your people and your technology mitigate the risks associated with security scams and other browser-based social engineering attacks.
Conclusion
Security support scams and other browser-based social engineering attacks are not going away any time soon. Scammers are exploiting older, trusted domains registered by recognized third parties like Microsoft, Amazon, or Digital Ocean to circumvent traditional security protections. Ensure your security awareness training is comprehensive and includes preparing employees to recognize social engineering attacks, including those initiated in the browser.
Lead Threat Researcher
Erin Kuffel