Keep Aware’s Threat Research function shares recent analysis of Canva designs and discuss their continued abuse for phishing.
Key Findings:
- Malicious actors are abusing Canva’s platform, likely to bypass traditional security tools that rely on a domain’s reputation.
- Abused Canva designs often center on viewing a document or, more specifically, a proposal.
- A malintent design will ultimately take a victim to another domain, often a phishing page.
- Common phishing pages attempt to harvest Microsoft credentials.
Canva, Another Abused Platform for Phishing
When designing new phishing schemes and campaigns, threat actors are known to piggyback off of commonly-used platforms’ domains and reputations, such as Microsoft Dynamics standalone marketing forms. Today, Keep Aware’s Threat Research division releases findings on yet another abused platform: Canva.
As a multi-purpose graphic design platform, Canva is a tool primarily used for marketing purposes. Free and paid users can create content – referred to as “designs” – in a variety of mediums: social media posts, posters, slide presentations, and more. These designs, hosted on Canva’s domain, can also be made available for others to view – and that is the feature phishers are abusing.
An Attack’s Stepping Stone
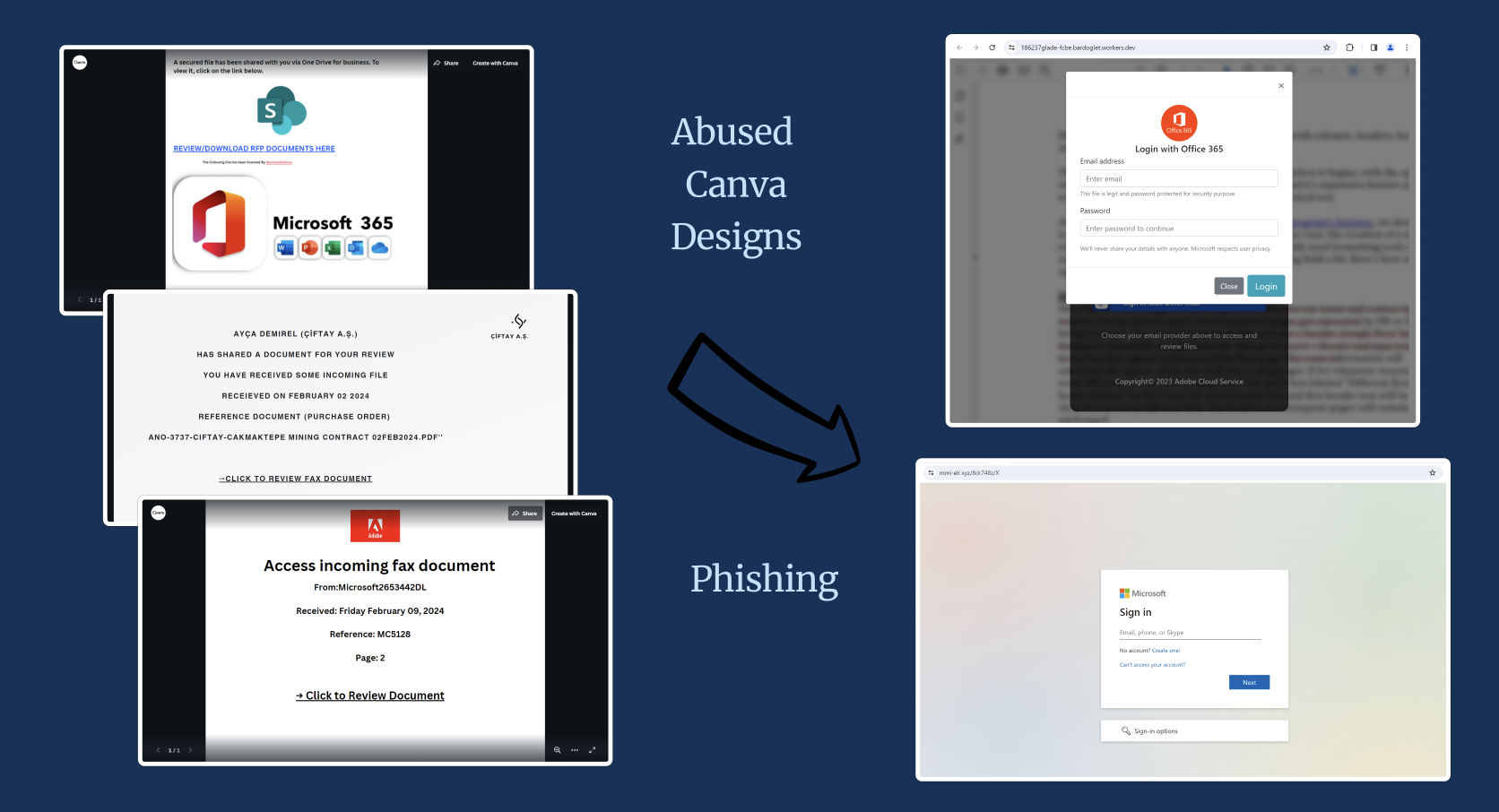
Phishing page creators are developing publicly-viewable Canva designs that appear as if a file or document is waiting for the user to download and/or review. Sent via email, links to these designs prompt unsuspecting victims to click a link that directs the user’s browser from canva.com to an attacker-controlled webpage – most prominently a Microsoft phishing page – on another domain. In essence, Canva’s platform is being used by threat actors as a stepping stone, or an intermediary step, in their phishing attacks.
Before delving into our analysis, we should mention that this is by no means a newly-abused platform. Phishing attacks have been reported using Canva designs for years. In 2020, Trend Micro reported phishing campaigns using the Evernote and Canva platforms; last year, Microsoft published an article outlining a business email compromise (BEC) attack that began – and extended its reach – with phishing links to a malicious Canva design.
In our recent research, we have confirmed that this platform is still being abused. Below, we outline our analysis of these malintent designs.
Phishing Theme: “Faxes” and “Documents” and “Proposals”, Oh My!
After reviewing 108 unique and active malintent Canva designs, we observed common traits in them; the designs:
- Are a single-page design (i.e., no scrolling or clicking through slides);
- Display logos of either Microsoft or Adobe, and/or appear as a company’s bid proposal;
- Focus on either a fax, a document, or, specifically, a proposal;
- Have language encouraging the user to click in order to view or download ‘the document’; and
- Display hyperlinked text or a full-page image that, when clicked, takes a victim to a malicious domain.
In the following sections, we show examples of malintent designs and a couple of their final phishing pages.
Examples, Malintent Canva Designs
This section provides many full-page screenshots of malicious Canva designs. In the below table, one column shows designs that appear to be bids, proposals, and/or requests for proposal (RFPs); in the other column are designs misusing Microsoft and/or Adobe logos. Though the table separates the two categories, note that many have overlap (e.g., a bid proposal design could also have Microsoft’s logo present).
| Bid Proposals / RFPs | Microsoft and/or Adobe Logos Present |
Also note that some designs make claims that the file is ‘secure’, ‘scanned by an anti-virus’, or is ‘safe’. Such claims, as shown in some of the above examples, include “The Following File has been Scanned by NortonAntiVirus” or “The document/file is protected by Adobe and safe to open”. For any website prompting you to download a file and making these types of claims, we advise you to disregard those claims, report the respective webpage (or Canva design) to your IT security team, and cease browsing on the site.
Examples, Final Phishing Pages
Once a user clicks on a design, the victim is taken to a phishing page on another domain. The most common attacks observed are those attempting to steal Microsoft credentials. Below are examples of these final phishing pages:
Why Canva?
Canva offers the functionality to create and publish designs on its domain for free user accounts. The ability for a threat actor to:
- Spend zero money and freely host an intermediary page that is
- Hosted on an older domain with a reputation for legitimate purposes
both likely contribute significantly to its abuse.
Canva’s domain reputation and its brand reputation can carry significant weight when encountered by tools and people, respectively. Collectively, there is a trust for platforms that are well-known and commonly-used for legitimate, and often business-related, purposes. Threat actors understand and exploit that trust.
Furthermore, as previously mentioned, reports of phishing attacks using Canva’s platform were first published years ago. Since the platform is still used by phishers, it seems reasonable to conclude that this tactic has been successful enough for malicious actors to continue their campaigns on Canva.
And though this research highlights one platform in particular, Canva is hardly alone. Keep Aware has also observed and stopped browsing threats originating from other collectively-trusted platforms, including Google Forms and Microsoft Dynamics 365.
Conclusion, Recommendations
To recap, our research into Canva designs reveals the platform is still being abused by malicious actors, and malintent designs are a stepping stone in phishing attacks. These designs are often a single page, with a button or an image that is hyperlinked to another domain, and has verbiage prompting the victim to click to ‘view a document or proposal’.
Canva is but one platform threat actors are abusing to host webpages in an attack sequence. Protect your organization against this and similar browser-based attacks by ensuring your security awareness program includes educating employees on identifying and reporting sites and emails prompting them to view or transfer business documents. Additionally, ensure there are technical controls in place to restrict access to known and emerging browsing threats, such as malintent Canva designs.
Learn about Keep Aware’s browser security solution and how we protect organizations from this and other browsing threats.
Lead Threat Researcher
Erin Kuffel