Key Findings:
- Threat actors are abusing Microsoft Dynamics 365 Customer Insights – Journeys standalone forms.
- Today, 1 in 5 forms are threats.
- Malicious standalone “forms” often do not look like forms.
- Malignant forms will redirect you to another domain.
- Captcha usage by malinent forms far outweighs legitimate forms usage.
Intro
For those in the cybersecurity industry, it likely comes as no surprise that applications and infrastructure of a ubiquitous company, such as Microsoft, will become a target for threat actors. Keep Aware’s Threat Research function’s recent research into Microsoft’s Dynamics 365 Customer Insights Journeys standalone forms shows that these forms are being abused with malintent and likely for phishing purposes.
This article delves into our analysis of the current landscape of Microsoft’s Dynamics 365 standalone forms, distinguishing between their legitimate use and their exploitation by threat actors. We share our collection methodology, present key insights, and illustrate interesting findings with the intent to provide an informative resource for understanding and mitigating this emerging cybersecurity and browsing threat.
Dynamics 365, Standalone Forms
Microsoft Dynamics 365 is a suite of enterprise software applications to manage a variety of business processes, including customer relationships, finance, and most notably for this article, marketing. Designed to streamline data collection and workflow management, Dynamics 365 has a marketing capability to create and publish forms that can be hosted either on a custom domain or on the Microsoft-owned subdomain, *.mkt.dynamics.com.
This article focuses on standalone forms published on Microsoft’s Dynamics marketing subdomain. These forms have the following URL pattern:
| assets-XXX.mkt.dynamics.com/<uniqueID>/digitalassets/standaloneforms/<uniqueID> |
Note that “XXX” denotes the geographical CDN, such as “usa”, “can”, or “ind”. The geographical CDNs encountered during this research – and their corresponding geographical area – are listed in the following table.
| Geographical CDN Acronym | Geographical Area |
| APJ | Asia Pacific |
| CAN | Canada |
| EUR | Europe |
| GBR | Great Britain |
| IND | India |
| OCE | Australia |
| SAM | South America |
| USA | United States of America |
Collection and Research Methodology
To gather a list of standalone forms indexed by Google’s search engine, we first performed the following Google search:
| site:dynamics.com inurl:standaloneforms |
Our Threat Research function visited each of the 100+ results, noting what the forms were prompting, following those prompts, and recording their subsequent redirects and final URLs. The following sections highlight three key insights of malicious Dynamics 365 standalone forms and visually illustrate other interesting findings.
Key Insight #1: Malicious Forms Are Not Forms
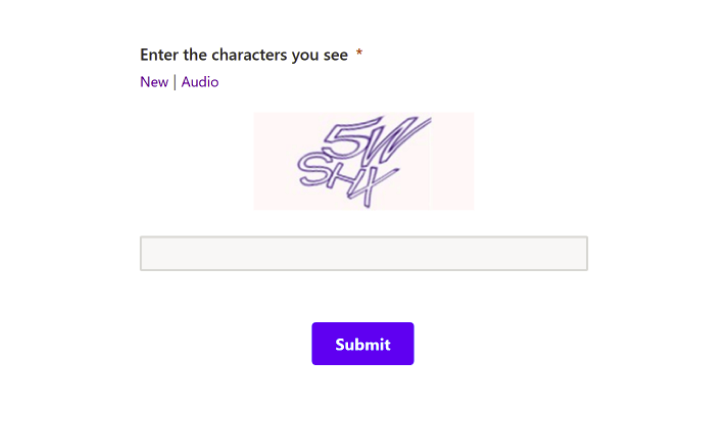
While a “form” implies a user (or victim) would encounter a document that contains fields in which one can write or select an option, most malintent standalone forms we encountered did not contain these fields. Commonly, the malicious forms would be very minimal pages with either:
- Just a captcha with a submit button, or
- A button that states something along the lines of “View Document”.
Legitimate forms have multiple fields for a user to fill out; they will have branding on their page, such as their logo; they contain a checkbox for the user to agree to subsequent communications; they often have a privacy policy in their form’s footer that links to their organization’s domain; and so on.
Below are example screenshots of legitimate standalone forms and of those that were confirmed malicious. Note the stark visual contrast between the two classifications.
Key Insight #2: Malicious Forms Ultimately Redirect To Malicious Domain
If a victim were to follow the prompts of the malicious forms (e.g., successfully passing the captcha, or clicking the button to ‘view a document’), they are ultimately redirected to a malicious domain.
During our research, we found that abused forms ultimately redirected a victim to either:
- Example.com (A benign site sometimes used to redirect those using a virtual machine or using a programmatic tool away from the actual malicious site);
- An error page on a domain not yet classified as malicious (But, the initial form and redirects mimicked the other attack chains);
- Microsoft login phishing page, specifically; or,
- An otherwise known-malicious domain.
Below is a visual breakdown of these findings.
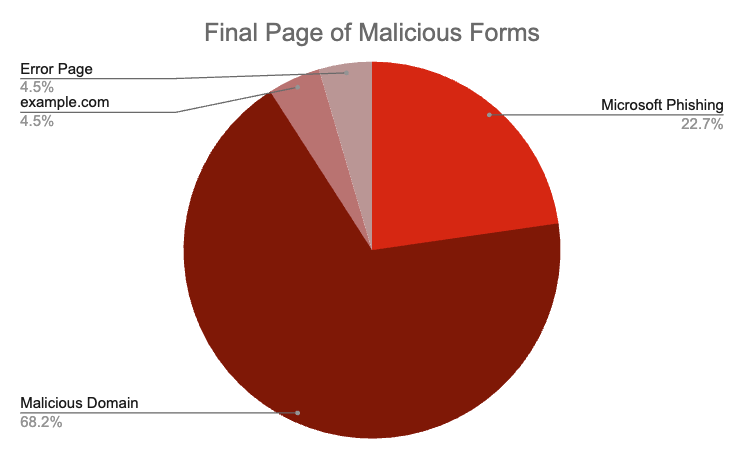
Worth noting is that, for the known-malicious domains that did not serve a specific threat page (e.g., a phishing page), these domains had already been classified by security vendor tools as malicious, most commonly as phishing, and thus were likely part of a previous phishing campaign.
Key Insight #3: Every 1 in 5 Forms are Threats
Standalone forms confirmed to be malicious accounted for approximately 23% of all forms hosted on Microsoft’s *.mkt.dynamics.com subdomain. In other words, in today’s threat landscape, if someone were to randomly visit a Microsoft Dynamics 365 standalone form, there is over a 1 in 5 chance that form poses a threat.
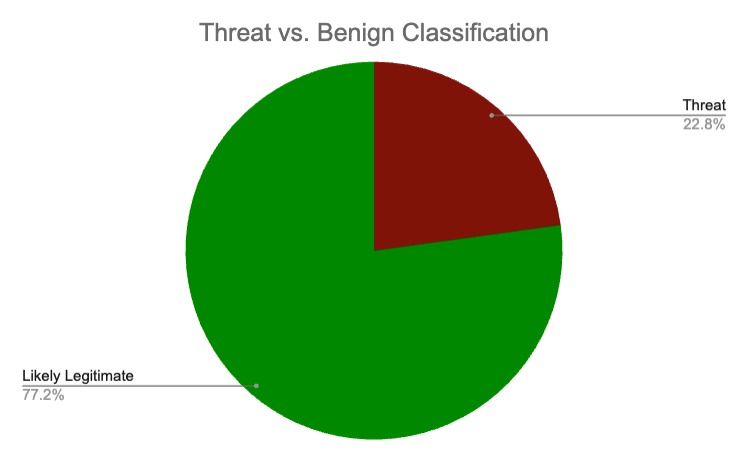
For a more detailed breakdown, see the following section, where we provide visual representations of the percentage of threat forms vs. likely legitimate forms for each of the eight geographical CDNs.
Other Interesting Findings
This section briefly presents three other interesting findings:
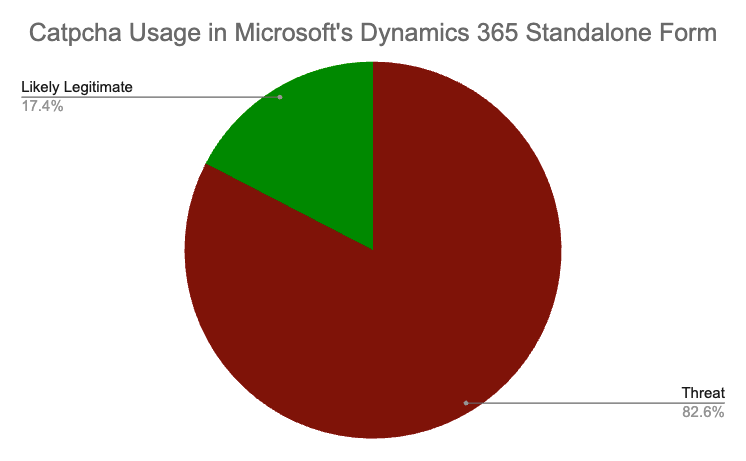
- Captcha usage among malicious forms greatly outweigh legitimate forms usage.
- Top level domains (TLDs) of final URLs are split rather evenly between .ru, .com, and CloudFlare buckets and workers (.r2.dev and .workers.dev).
- Europe’s CDN has the most percentage of legitimate forms.
Captcha Usage by Malicious Standalone Forms Greatly Outweigh Legitimate Ones.
TLDs of Final Webpage of Malintent Forms Split Rather Evenly Between “.ru”, “.com”, and CloudFlare Buckets and Workers.
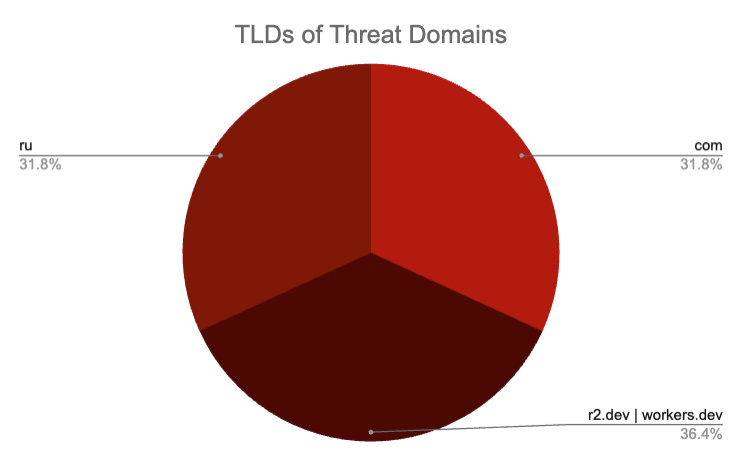
Note: Some domains’ TLDs were counted multiple times because multiple forms ultimately redirected to that same domain.
Europe CDN Has the Highest Percentage of Legitimate Forms;
USA Has the Lowest.
* Although the IND and SAM CDNs technically have the highest and lowest percentages, respectively, of legitimate forms, we encountered an incredibly small number of each (1 form and 3 forms, respectively) and thus err on the side of caution to announce them as the reigning CDNs.
| Geographic CDN | Visual Breakdown of Threat vs. Legitimate Forms, In Decreasing Order of % of Legitimate Forms |
| IND * | |
| EUR | |
| GBR | |
| OCE | |
| CAN | |
| APJ | |
| USA | |
| SAM * |
Conclusion, Recommendations
To recap, our research into Microsoft Dynamics 365 Customer Insights Journeys standalone forms has revealed three critical insights into the current threat landscape.
- First, many malicious forms disguise themselves by lacking typical form characteristics, often presenting just a captcha or a misleading button, in stark contrast to legitimate forms which feature multiple fields and branding elements.
- Second, these malignant forms frequently redirect users to malicious domains, including phishing sites and domains already flagged for malicious activities.
- Third, a significant portion, about one in five, of the standalone forms hosted on the *.mkt.dynamics.com subdomain during our research were malintent, underscoring the prevalence of this emerging threat.
To safeguard your organization against abused forms, ensure your security awareness program includes educating employees on identifying and reporting odd forms and suspicious websites and consider implementing technical controls that block access to known and emerging malintent webpages, including abused Microsoft Dynamics 365 Customer Insights Journeys standalone forms.
Learn how Keep Aware’s browser security solution protects people from this and other browsing threats.
Lead Threat Researcher
Erin Kuffel
IOCs
Malicious Dynamics 365 Standalone Form URLs
| Dynamics 365 URL |
| https://assets-apj[.]mkt[.]dynamics[.]com/6dd6bab0-28b3-ee11-9075-002248ed648d/digitalassets/standaloneforms/72e865ef-28b5-ee11-a568-6045bd58b969?aXNhYWMucG9vcmVAaWcuY29t |
| https://assets-apj[.]mkt[.]dynamics[.]com/7899cff2-ecb9-ee11-9075-000d3a80bc94/digitalassets/standaloneforms/03d2b868-c7ba-ee11-9078-6045bd58b6cb |
| https://assets-apj[.]mkt[.]dynamics[.]com/b06d6f6e-0db9-ee11-9075-002248ed649f/digitalassets/standaloneforms/be118203-29ba-ee11-9078-00224816d61b |
| https://assets-can[.]mkt[.]dynamics[.]com/1c1c3c15-98ab-ee11-a565-0022486db9f4/digitalassets/standaloneforms/fd22ce92-a9ab-ee11-a569-000d3af4e16d |
| https://assets-can[.]mkt[.]dynamics[.]com/6a05020d-d2ad-ee11-a565-0022486dbff0/digitalassets/standaloneforms/f0581aba-faae-ee11-a569-000d3af4e16d |
| https://assets-eur[.]mkt[.]dynamics[.]com/3dafdad1-01ba-ee11-9073-000d3ab8db5c/digitalassets/standaloneforms/75fb91dc-21bc-ee11-a569-000d3ad9b499 |
| https://assets-gbr[.]mkt[.]dynamics[.]com/063a532d-f8ae-ee11-a564-6045bdcf3dab/digitalassets/standaloneforms/89e88478-20af-ee11-a569-6045bd0cf992 |
| https://assets-gbr[.]mkt[.]dynamics[.]com/f4d89121-93b3-ee11-a564-6045bdcf3dab/digitalassets/standaloneforms/eef563bc-a1b3-ee11-a568-6045bd0cf003 |
| https://assets-oce[.]mkt[.]dynamics[.]com/916070d4-8abb-ee11-9075-002248932ac4/digitalassets/standaloneforms/2f600d3c-b2bb-ee11-9078-00224892c767 |
| https://assets-oce[.]mkt[.]dynamics[.]com/916070d4-8abb-ee11-9075-002248932ac4/digitalassets/standaloneforms/73e86c56-59bc-ee11-9079-00224892c767 |
| https://assets-sam[.]mkt[.]dynamics[.]com/79ed0346-43b5-ee11-a565-002248debde7/digitalassets/standaloneforms/c962eaaa-4eb5-ee11-9077-6045bd3a7e19 |
| https://assets-sam[.]mkt[.]dynamics[.]com/8bdf85a9-62bb-ee11-9076-6045bd3ad0e6/digitalassets/standaloneforms/b79c128a-6cbb-ee11-9078-000d3a8914e9 |
| https://assets-sam[.]mkt[.]dynamics[.]com/b8a50830-e9ae-ee11-a565-6045bd3ad0e3/digitalassets/standaloneforms/23fbc5c3-f6ae-ee11-a569-002248372b2a |
| https://assets-usa[.]mkt[.]dynamics[.]com/513d7b79-3cae-ee11-be32-000d3a106521/digitalassets/standaloneforms/a3b7f31d-b5ae-ee11-a569-0022482bdf37 |
| https://assets-usa[.]mkt[.]dynamics[.]com/52a9477c-8fb4-ee11-a564-000d3a35770e/digitalassets/standaloneforms/9e370bbb-9cb4-ee11-a569-000d3a337946 |
| https://assets-usa[.]mkt[.]dynamics[.]com/6dfb454a-6ebb-ee11-9075-6045bd00300a/digitalassets/standaloneforms/b409727d-aabb-ee11-a569-000d3a331f4f |
| https://assets-usa[.]mkt[.]dynamics[.]com/707a44a2-d9ae-ee11-be32-000d3a106c39/digitalassets/standaloneforms/3ddc47ee-9baf-ee11-a569-000d3a8bc887 |
| https://assets-usa[.]mkt[.]dynamics[.]com/86c785e8-c4b9-ee11-9075-6045bd003008/digitalassets/standaloneforms/1e1a1fb8-b3ba-ee11-a569-0022480b88ac |
| https://assets-usa[.]mkt[.]dynamics[.]com/ba1e741c-b3b4-ee11-a564-000d3a35773a/digitalassets/standaloneforms/b8272857-26b9-ee11-a569-000d3a320d06 |
| https://assets-usa[.]mkt[.]dynamics[.]com/ba426d85-5bbb-ee11-9073-000d3a13020b/digitalassets/standaloneforms/b35fe13d-96bb-ee11-a569-000d3a56562e |
| https://assets-usa[.]mkt[.]dynamics[.]com/cb97b262-70bb-ee11-9075-6045bd01663d/digitalassets/standaloneforms/542548f9-95bb-ee11-a569-000d3a347731 |
| https://assets-usa[.]mkt[.]dynamics[.]com/f299d1e5-f7b9-ee11-9075-6045bd003f2d/digitalassets/standaloneforms/51a8019a-09ba-ee11-a569-000d3a31a5df |
Malicious Final Domains
| Final Domain |
| 0nm[.]805nmzg[.]ru |
| 0rj[.]4c518kb[.]ru |
| 51t4ovhtnshk-1323921533[.]cos[.]sa-saopaulo[.]myqcloud[.]com |
| a464efb9[.]26b63b4fc3b75d50cd059892[.]workers[.]dev |
| b372299b[.]7e052f615df51fdc35d81f69[.]workers[.]dev |
| design[.]bloustaici[.]ru |
| eciconstructoss[.]com |
| f2gp54zayunw-1323563947[.]cos[.]na-toronto[.]myqcloud[.]com |
| ffb5e967[.]lijexab250[.]workers[.]dev |
| jwzgv2bnorcffu[.]zn8yeeu[.]ru |
| mcweeskrqkd[.]bdcvjhwbedhwbecwebd[.]ru |
| omerconsultings[.]com |
| portal[.]oracrat[.]ru |
| pub-2eef0dd9364d4248b298f5e4c6db0eb4[.]r2[.]dev |
| pub-9b9b412eca1b495da5d2ef734a2ea144[.]r2[.]dev |
| pub-e2afc8f4235b4d54bc4f507ed44d4ba8[.]r2[.]dev |
| s0bcpjmgyf54-1323921533[.]cos[.]ap-singapore[.]myqcloud[.]com |
| tt4n1o6ak9fapyzss2[.]batqmqy6[.]ru |

