A Link, Click, and a Phish Away! Using Legitimate Domains for a Multi-Step Phishing Attack
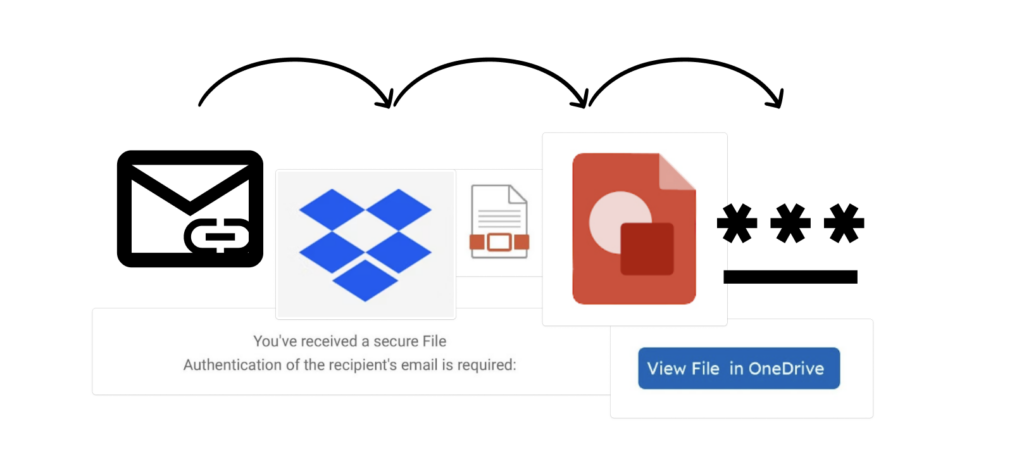
Key points: Overview Keep Aware has observed phishing attacks that use legitimate domains to host links that eventually lead to a credential stealing web page. This article focuses on commonalities between two recent phishing attacks that require a victim to click links on multiple legitimate domains before ultimately landing on a fake login page. This […]
“Looking” for Documents? .. “Look” No Further: A New Trend in Abusing Google Looker Studio for Phishing

Keep Aware has uncovered evidence that Google Looker Studio is being abused by bad actors to host intermediate phishing pages.
Cloudflare R2, Public Buckets and a Phishing Binge: An Analysis of Today’s Threat Landscape

Cloudflare public R2 buckets are being abused to host phishing pages.
Clicking Links, From Canva Design to Phishing Site: An Analysis of Today’s Threat Landscape
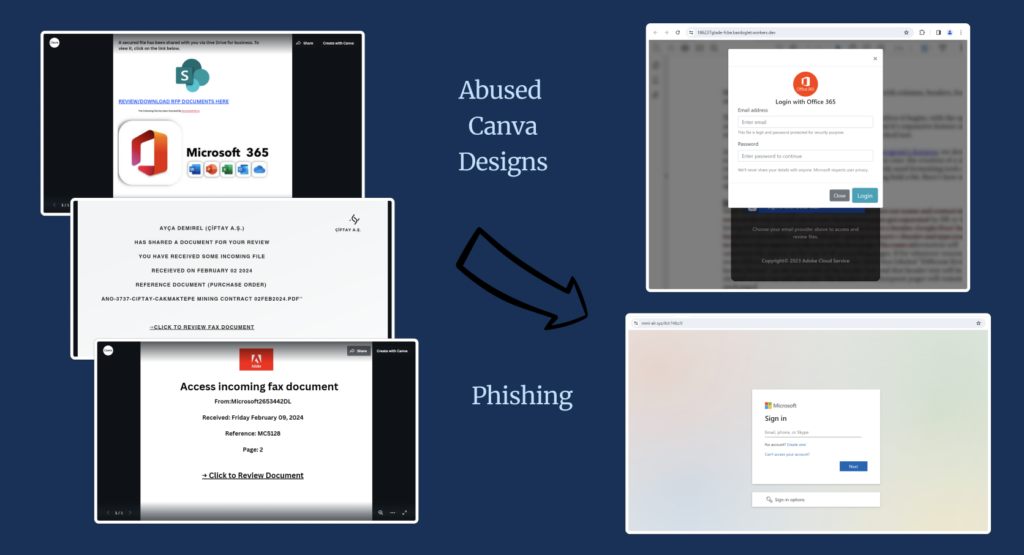
Keep Aware’s Threat Research function shares recent analysis of Canva’s platform abuse for phishing purposes.
The Abuse of Microsoft Dynamics 365 Standalone Forms: An Analysis of Today’s Threat Landscape

An analysis of Microsoft Dynamics 365 standalone forms reveals that, in today’s browsing threat landscape, 1 in 5 forms are threats.
AI and Zero-Day Phishing: Combating The Evolving Browser-Based Security Challenges

With the rise of generative AI usage across industries, no one should be surprised this trend also applies to the cybercriminal industry. They, too, are integrating AI into their workflows to ultimately increase productivity. This new technological integration into cyber criminals’ and other threat actors’ operations have many IT security professionals left wondering: Before we […]
Understanding Security Support Scams: A Comprehensive Analysis
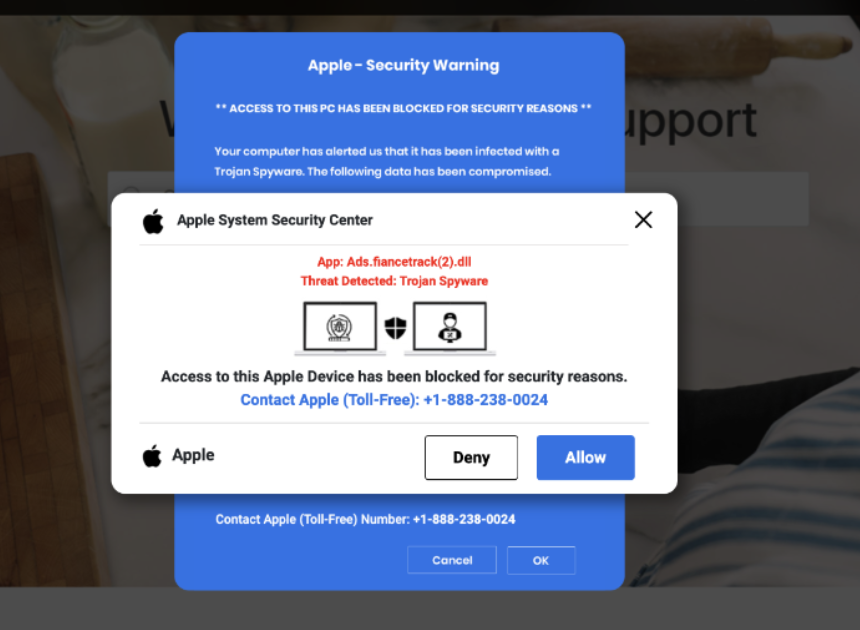
Key Topics and Findings: Overview In today’s interconnected world where practically all employees use the internet, the prevalence of security support scams and other social engineering sites remains a concern. In a threat post specifically about Microsoft security scam websites, our Threat Research team discussed recent web pages impersonating Microsoft that are falsely claiming a […]
From Google Search to Microsoft Security Scam
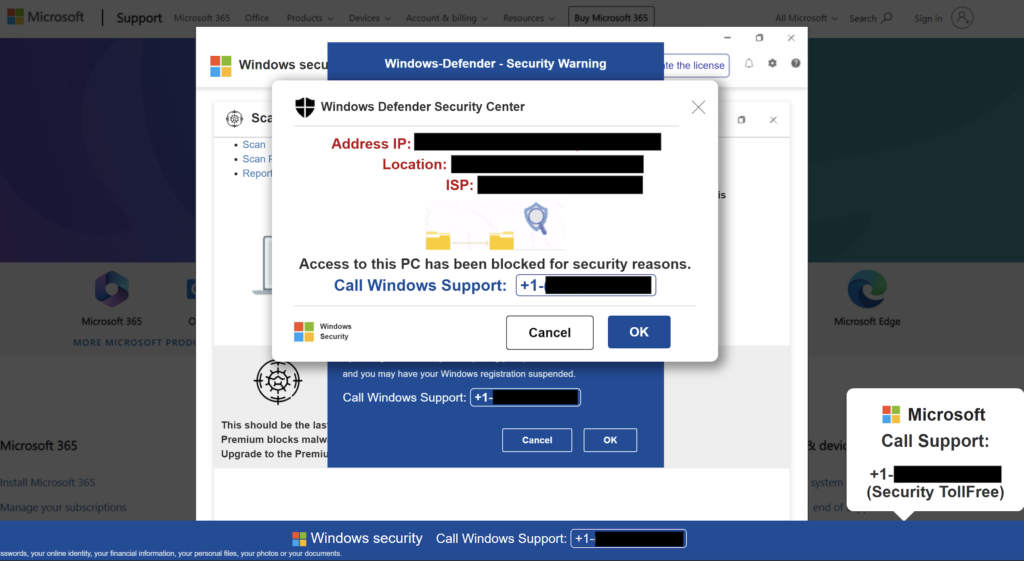
Key Findings: Overview Keep Aware’s Threat Research division identified a recent batch of fraudulent Microsoft support sites. While these scam campaigns are not novel, they persist as an online security risk for all internet users. The scam sites impersonate Microsoft, deceive the user into thinking their machine is infected, and prompt the user to call […]
Browser Notifications Hijacking via DDoS-Protection Mimicry
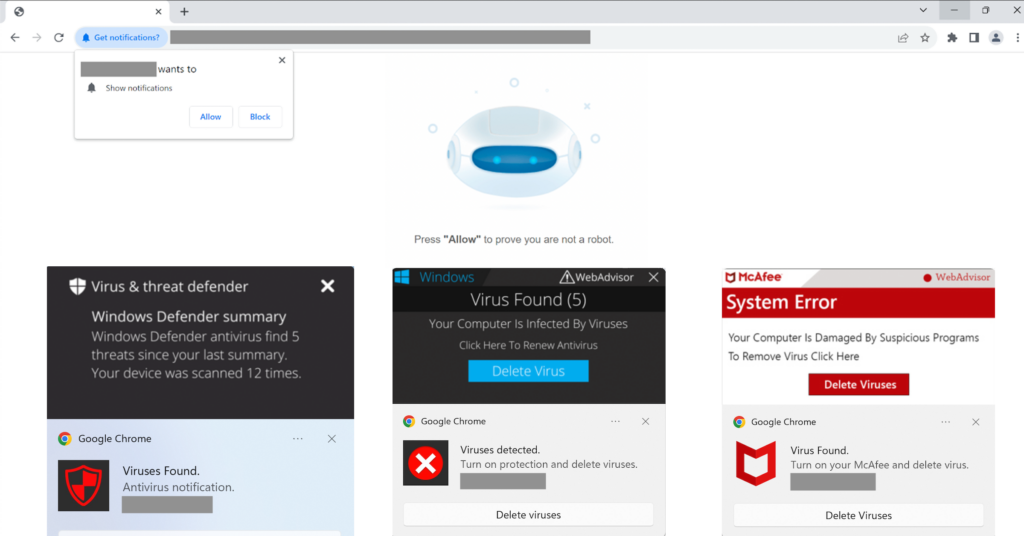
Key Findings: Overview Keep Aware’s Threat Research team has identified a browser notifications hijacking campaign that impersonates a Russian-based distributed denial of service (DDoS) protection company’s challenge page. This campaign tricks the user into allowing browser notifications and subsequently bombards them with dubious notifications, masquerading as McAfee or Windows Defender alerts, falsely claiming that the […]
Addressing the Risks of Using Prompt-Based AI Tools: A Proactive Strategy

Key Takeaways: Employees are Capitalizing on Prompt-Based AI Tools There has been a trend across industries where businesses are flocking to integrate AI into their technology stack, with the ultimate goal of increasing efficiency and/or efficacy. Alongside this trend, though, employees have been integrating prompt-based AI tools, such as OpenAI’s well-known tool ChatGPT, into their […]
