Taking a moment or pausing before taking action is not a new concept; it is ingrained in all of our technology. It is an essential part of any interface and in the realm of cybersecurity, especially browser security, it can play a more significant role. Most confirmations or pauses lack context; the same critical action gets the same response, “Are you sure?..” Whether you are asked to delete a file or perform any other action, the message remains the same across platforms. This one-size-fits-all approach does not align with the varying risk levels across companies, departments, and individuals. So, while we recognize the potential of pause, the question is: How can security teams effectively apply this idea to bolster cybersecurity? The answer lies in pinpointing where risks occur during your employees’ workday and integrating a flexible solution that empowers both your IT security team and employees to stay secure.
The Power of Pause
“The Power of Pause” refers to utilizing the deliberate act of taking a moment to consider the potential consequences of one’s actions to promote better decision making. It’s a strategy aimed at preventing mistakes and it is often applied to human-computer interactions to stop inadvertent data loss.
This concept could be better applied to cybersecurity and could emphasize the importance of critical thinking and mindfulness in online interactions. It is not uncommon for an IT team to encourages their employees to verify the legitimacy of websites and email requests, check for secure connections (https://), and question suspicious online behavior, but even Google has removed some of the “go-to” methods for doing these checks. Where there is risk, the power of pausing activity can be extremely effective in reducing the risk of the situation. Ultimately, this can empower individuals and organizations to make informed, security-conscious decisions in their everyday work, reducing the likelihood of cyberattacks and their potentially devastating consequences. To execute a strategy around pausing, like any critical action plan, security teams need to observe the risk in your own environment, identify areas of the highest risk and implement solutions that reduce those risks while also measuring their impact over time. This last part requires adaptability which means solutions need to be hyper-flexible to the organization and certain departments, and there are a few tips to consider.
A Quick Example
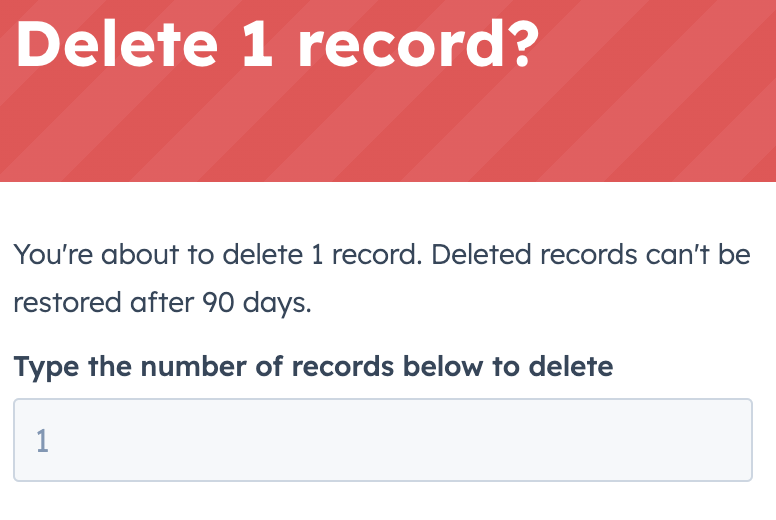
Pauses exist in all of our work. Outside of security, these are mostly implemented for productivity and inadvertent data loss cases. In the example below, I can clearly acknowledge I’m about to delete one item. However, if I receive this every time I want to delete, it becomes less effective especially since “1 record” could mean anything. A file, an employee record, an entire server, etc.
Tips for an Effective Pause
Be Specific, but Keep it Simple
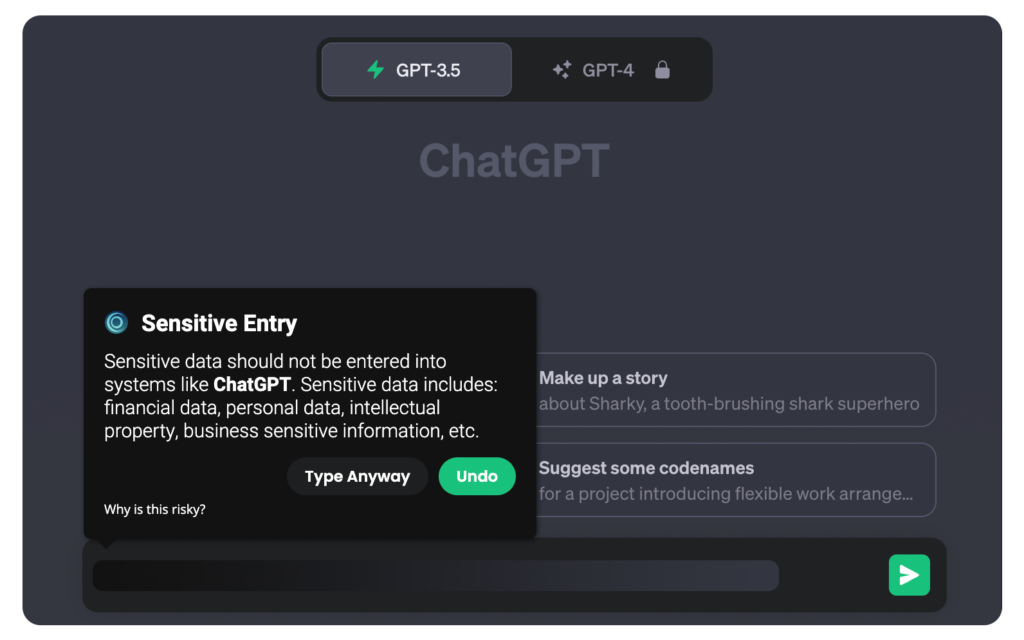
When implementing a strategy to focus on pausing critical and unusual behaviors, it is essential to be specific and keep the explanations simple. Instead of merely asking if someone is sure about an action, take this opportunity to explain the associated risks in plain language. For example, if an employee is using AI tools like ChatGPT, provide them with clear guidance on potential pitfalls, such as sharing sensitive information inadvertently. This is ultimately the first key piece to a strategy that Exposes, Educates and Enforces safer cybersecurity practices across your organization.
Make It Easier to Be Secure
Make sure you simplify the process of understanding and accepting the risks associated with various actions. This starts with that simple policy around sharing sensitive information, but it takes it a step further by including context, or why it is suspicious, in clear and concise language. You can use this language in notifications and prompts to help your employees grasp the potential business consequences of their choices. Employ visual cues that align with the user interface and the given task to enhance comprehension, making it easier for people to make informed decisions that prioritize security. Again, that “Are you sure?” message is a lot more meaningful when its backed by why you are even asking in the first place. To name a few…
- Your department rarely shares files this way!
- You have never logged into this site!
- This extension is able to read your banking information!
Some Activities can be too Risky
It’s important to recognize that certain activities may pose risks that your security team cannot accept. For instance, if an employee attempts to share a file on an unlicensed platform like WeTransfer when its clear Google Drive should be used, the security software should not only block the action but also provide guidance on secure alternatives. By directing employees to approved tools and explaining why they are safer, you ensure that even in high-risk scenarios, employees are guided toward more secure practices. Alternatively, these measures could result in someone further clarifying why that activity is aligned with a business case. Security solutions need to better align with these workflows.
The Browser as the Key Workspace
People have always been the key pathway to an organization’s critical assets, but the evolution of modern work has made it more accessible for an adversary to attack an organization through its people. Everything we do now happens through a single application – logins, critical data entities, uploads and downloads. The browser is a key component of the attack surface for modern business. Despite the implementation of security controls around the browser, the workforce remains vulnerable to sophisticated, people-targeted threats. What seem like simple, benign activities are often taken advantage of and proof a risk to an organization. Here are few that we have seen:
- Download utilities like printer drivers, screen recorders, or extensions to shortcut or perform a task
- Navigate to a certain software or documentation on a software
- Share files with a personal file storage account
For the same reasons attackers can manipulate the browser landscape with little scrutiny, security teams are able to create secure experiences for their employees. IT security teams have the power to transform both suspicious and secure interactions for their employees. The browser is flexible and exposing the technologies behind it to security teams allows them to better secure credential, file sharing and download activities.
The Power of Pause in Cybersecurity
These are a few examples of how the “power of pause” can be applied to cybersecurity and specifically the web browser. Attackers have long exploited various software systems to obscure their true intentions, and redirecting web traffic is a tactic that continually evolves especially in an era where companies eagerly track people for advertising purposes. Here’s just a few from the last couple of months:
- LinkedIn Smart Links Abuse
- Google Ads that Push Malware and More Google Ads that Push Malware
- Redirects to push Fake Browser Notifications
Bringing a pause to these types of attempts is a strategy that can be tailored to your organization’s unique risk profile. For example, we can make sure someone knows and acknowledges where they are actually going for unknown threats:

To take it a step further, Keep Aware applies pausing to certain critical actions in the browser. This can be specified for specific logins, downloads, extensions, and individual browsing activities like the ones mentioned above.
Where Security Awareness and Productivity Come In
Educating your employees plays a pivotal role in enhancing an organization’s cybersecurity posture. It is well known that people serve as the first line of protection against cyber threats, and their awareness of potential risks and safe online practices is paramount in reducing the risk of a successful cyber attack.
The browser is the optimal platform for implementing the power of pause due to its ubiquity in employees’ work activities. Educating people within the browser environment ensures immediate retention and application of cybersecurity knowledge when confronted with risky situations when those benign behaviors are taken advantage of by attackers.
Browser Safeguards with Keep Aware
Keep Aware browser security can display a native security experience across any browser and provide explanations about associated risks when your employees run into risky situations, empowering them to make informed, secure decisions. Keep Aware offers highly customizable responses to threats across the browser landscape. IT security teams seamlessly integrate features like prompts, tooltips, and other interactive experiences, guiding employees towards safer practices.
In a world where the threat landscape is ever-evolving, solutions that focus on people are essential for organizations aiming to stay one step ahead of unknown threats while maintaining seamless productivity. Keep Aware provides customizable patterns that strike the delicate balance between robust security and unhindered employee workflows. Human error remains a leading cause of data breaches, and the “power of pause” in security proves to be a crucial tool. Taking a moment to observe and adapt can mean the difference between a security gap and resilience in the face of today’s cybersecurity challenges.
Ryan Boerner on LinkedIn
Ryan Boerner