
“BitB vs. BitM vs. AitM vs. AitB.” Same letters, different order, and very different threats.
These acronyms get thrown around in articles and vendor decks, sometimes interchangeably. For security teams responsible for protecting users in the browser, clarifying that confusion matters. This post is a quick reference to help you keep them straight, understand how they work, and where Browser Detection & Response (BDR) solutions help.
Acronyms at a Glance: What’s the Difference?
All four techniques are commonly used in phishing and credential theft:
- BitB — Browser-in-the-Browser
- BitM — Browser-in-the-Middle
- AitM — Attacker-in-the-Middle
- AitB — Attacker-in-the-Browser
These terms overlap in goals (credential or session theft) but differ in where the attacker sits and what the user is actually interacting with.
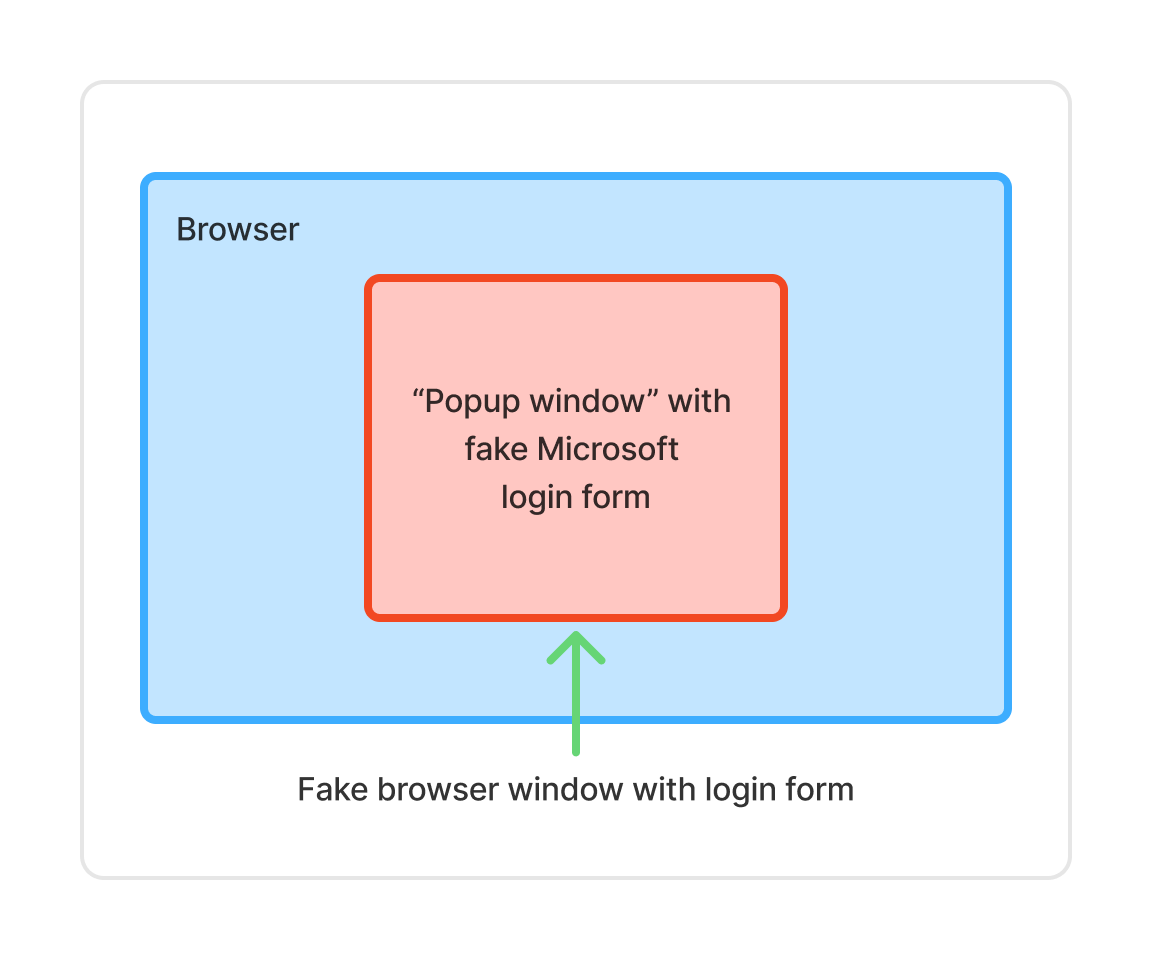
(BitB) Browser-in-the-Browser: User Logs In Using a Fake Browser or Popup
What it is: A fake browser window rendered inside a web page to impersonate a trusted login flow (e.g., Microsoft, Google, Okta, etc.).
The pop-up looks real—address bar, padlock, branding—but it’s just HTML, CSS, and JavaScript controlled by the attacker. A more fitting name might be “(fake)browser-in-the-browser”.
Why it works:
- Users are trained to expect pop-up SSO windows
- The pop-up browser window is fake but convincing
- No malware required—pure web content
Common implementation details:
- Custom HTML/CSS/JS
- Sometimes delivered via iframes
Bottom line: BitB = a fake login window pretending to be a real browser.
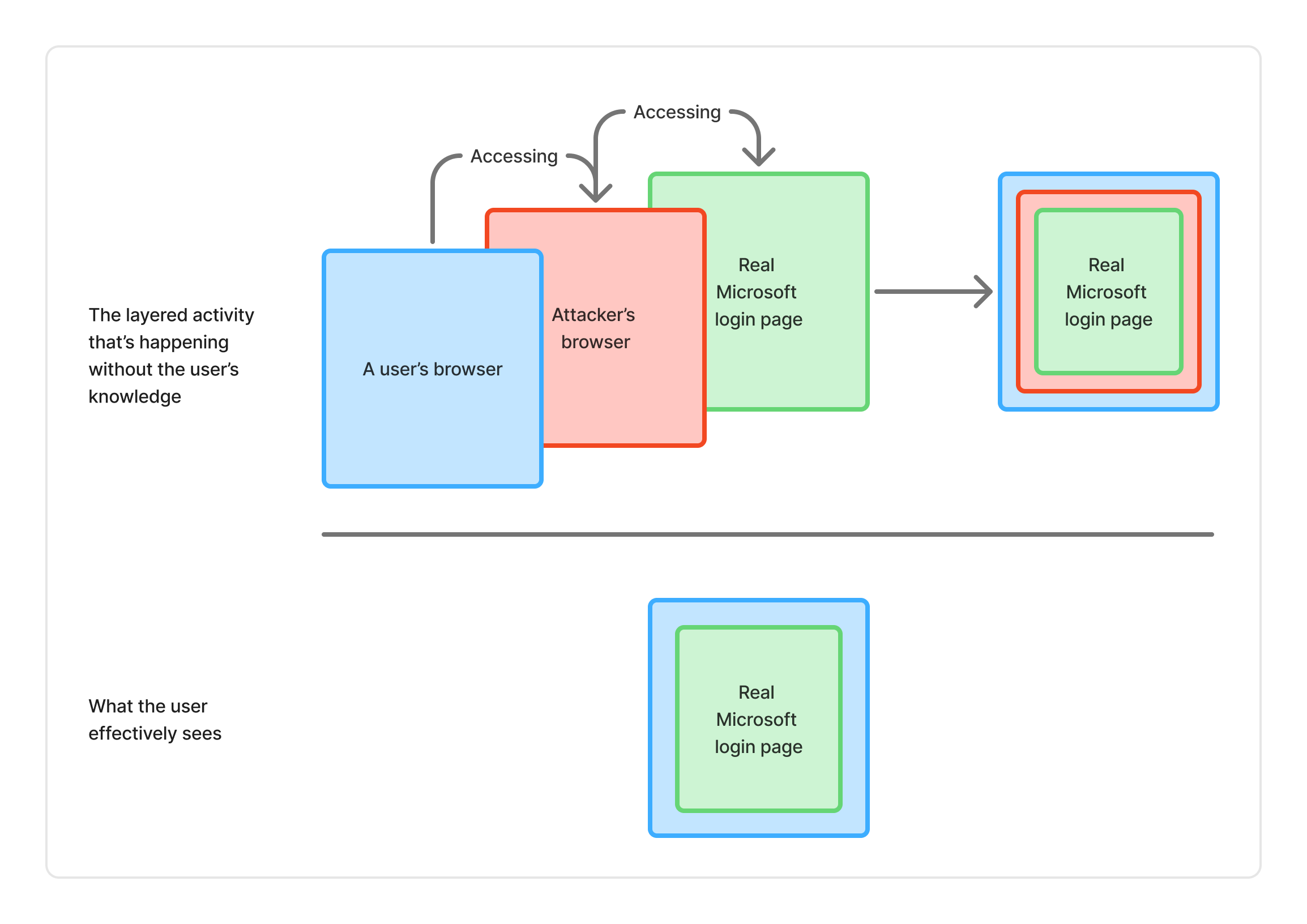
(BitM) Browser-in-the-Middle: User Logs In Using a Remote Browser
What it is: A user logs into a real website, but through an attacker-controlled remote browser.
From the user’s perspective, everything works as expected: real domain; real login; real MFA challenge.
But the session is created inside the attacker’s browser, not the user’s. In other words, the session token is stored on the attacker’s browser, not the user’s.
Why it works:
- MFA succeeds because the attacker relays credentials in real time
- Session cookies and tokens remain accessible to the attacker
- No endpoint compromise required—it’s pure web content
Think of it like a malicious version of remote browser isolation (RBI)—you’re browsing using someone else’s browser.
Bottom line: BitM = Authentication using an attacker’s browser, not your own.
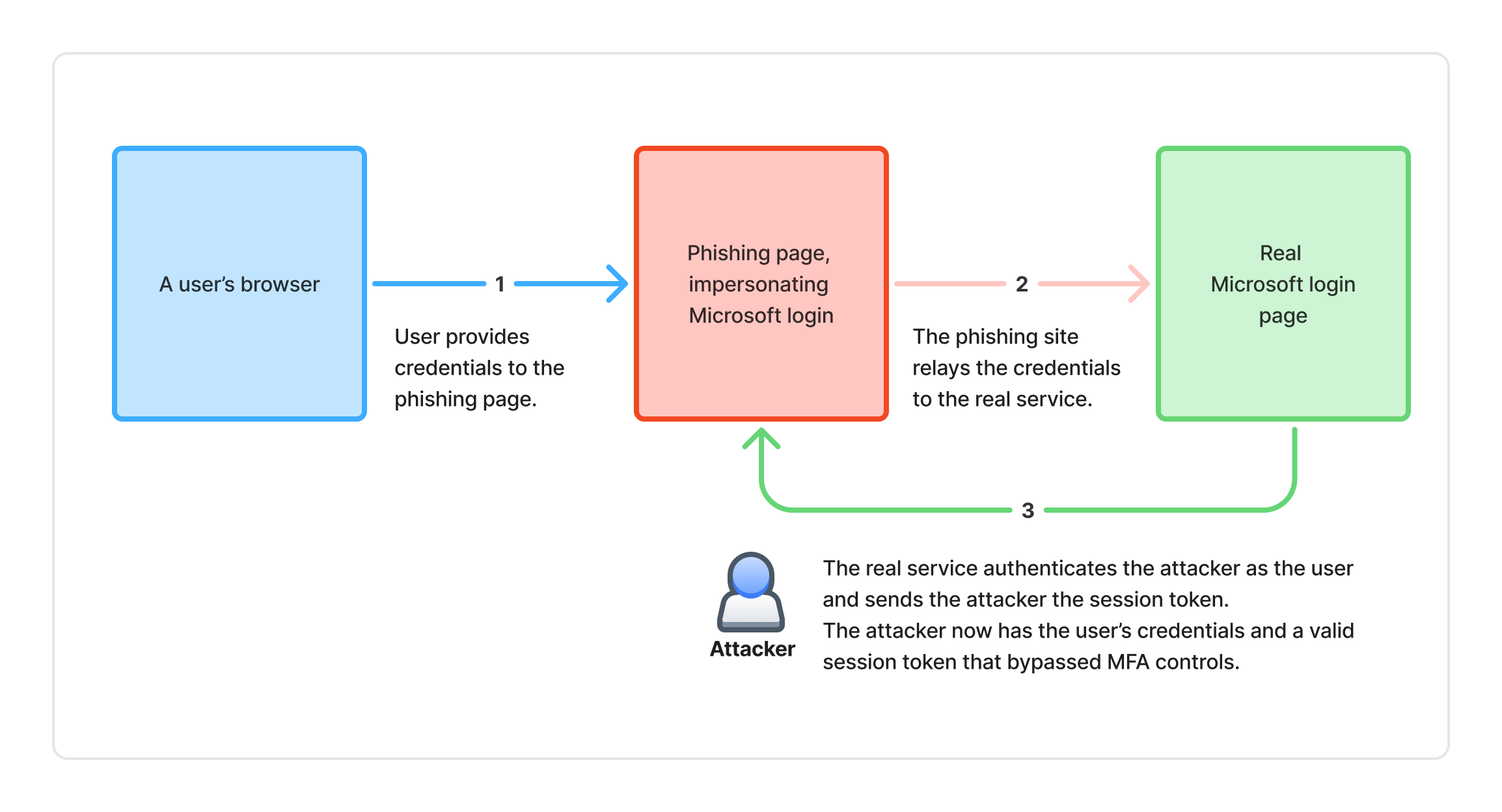
(AitM) Attacker-in-the-Middle: Attacker Intercepts Logins
What it is: A broader category where the attacker intercepts and sometimes relays traffic between the user and a legitimate service.
BitM is effectively a specialized browser-based AitM relay attack, but AitM can also include:
- Reverse proxies
- Phishing frameworks (e.g., Tycoon 2FA phishing kit pages)
- Token replay attacks
Why it works:
- Credentials and MFA are captured in transit and bypassed
- Session tokens are stolen post-authentication
Bottom line: AitM = the attacker transparently sits between you and the real site.
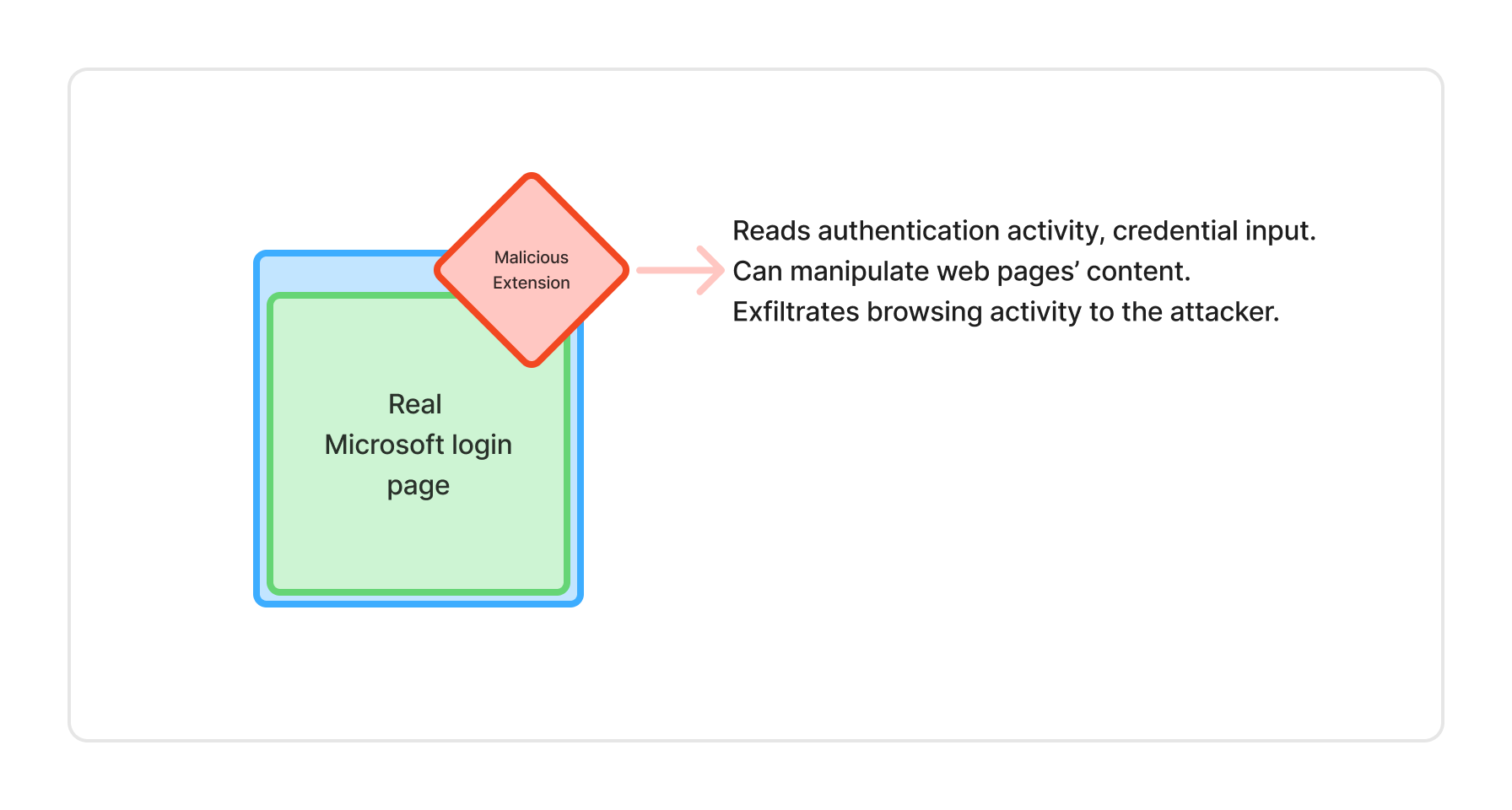
(AitB) Attacker-in-the-Browser: User’s Browser is Compromised
What it is: The attacker is already inside the user’s browser environment.
This typically involves:
- Malicious browser extensions
- Injected JavaScript, which the browser executes
Why it works:
- An attacker can silently read and modify page content
- Credentials, form data, and sessions are exposed to the attacker
- Often invisible to the user and to traditional security tools
Bottom line: AitB = the browser itself is compromised.
Definitions Recap
- BitB — Fake browser login window inside a web page
- BitM — Login happens in an attacker-controlled remote browser
- AitM — Attacker intercepts traffic between the user and the site
- AitB — Attacker operates from within the user’s browser
Different mechanics. Same end goal: credential or session theft.
Where Traditional Controls Fall Short
Email and network security, MFA, and endpoint protection often miss these attacks because:
- The domains may be legitimate or of good reputation
- MFA is successfully bypassed
- No malware is dropped
- The browser is the attack surface
This is why browser-level visibility matters.
Where BDR Helps
BDR solutions are strongest when detecting and investigating attacks that occur in the commonplace interface that attackers use to spy on users and steal credentials—the browser. BDR tools are uniquely positioned to provide the missing coverage of browser-based attacks. They can:
- Detect fake login pages (BitB, BitM, AitM)
- Identify suspicious browser and extension activity (BitM, BitB, AitM, AitB)
- Observe credential prompt anomalies (BitB, BitM, AitM, AitB)
- Correlate chained phishing activity (BitB, BitM, AitM)
When combined with network and endpoint controls, BDR provides the additional coverage needed for security teams to effectively defend against all four of these types of browser-based attacks.
How Keep Aware’s BDR Addresses These Attacks
Keep Aware focuses on what the user actually sees and interacts with in the browser, not just network-level activity.
Specifically, Keep Aware helps by:
- Detecting fake browser UI elements used in BitB attacks
- Identifying remote-browser usage patterns consistent with BitM
- Correlating suspicious login flows across chained phishing pages
- Providing investigators with browser-level evidence—not assumptions
Instead of guessing where the attack started, security teams can see:
- What the user clicked
- What the page rendered
- What credentials were provided
Final Thoughts
Don’t let acronym overload distract from the fundamentals.
Whether it’s BitB, BitM, AitM, or AitB, the attacker’s ultimate goal remains the same: collect credentials or hijack a session without triggering traditional controls.
What matters most isn’t perfectly classifying the technique, but having reliable browser-level signals that confirm a phishing event occurred, even when email security, MFA controls, and network defenses see nothing wrong.
That’s where modern BDR—and Keep Aware in particular—adds value by delivering high-quality alerts and actionable browser telemetry that give security teams confidence that an attack occurred and how it unfolded.



