
An email about updated 2025 fiscal year benefits, sent through a business management platform, led an employee to a malicious site designed to steal work credentials. What looked like a normal business email slipped past every early control—until browser-native security detected it.
Phishing Chain: Monday.com WorkForm Credential Theft
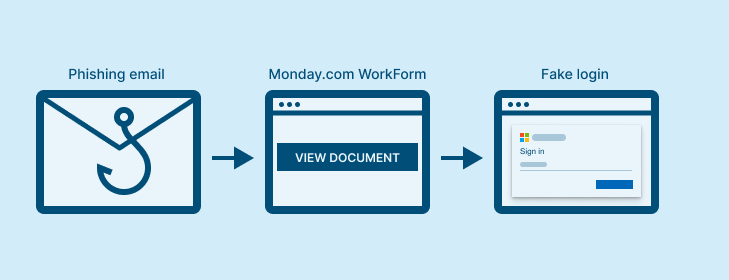
A Friday afternoon, near the end of the workday, an employee opened an email sent from the reputable DaySmart domain, a business management platform. Claiming their benefits and compensation will be updated for the 2025 fiscal year, the user was prompted to click a link to review the updates.

The employee’s browser opened a simple Monday.com WorkForm, titled “Update: Your 2025 Employee Report”, nudging the user to click yet again to view the document.

The next call to action encourages the employee to provide their Microsoft business email address, ultimately attempting to steal work credentials.
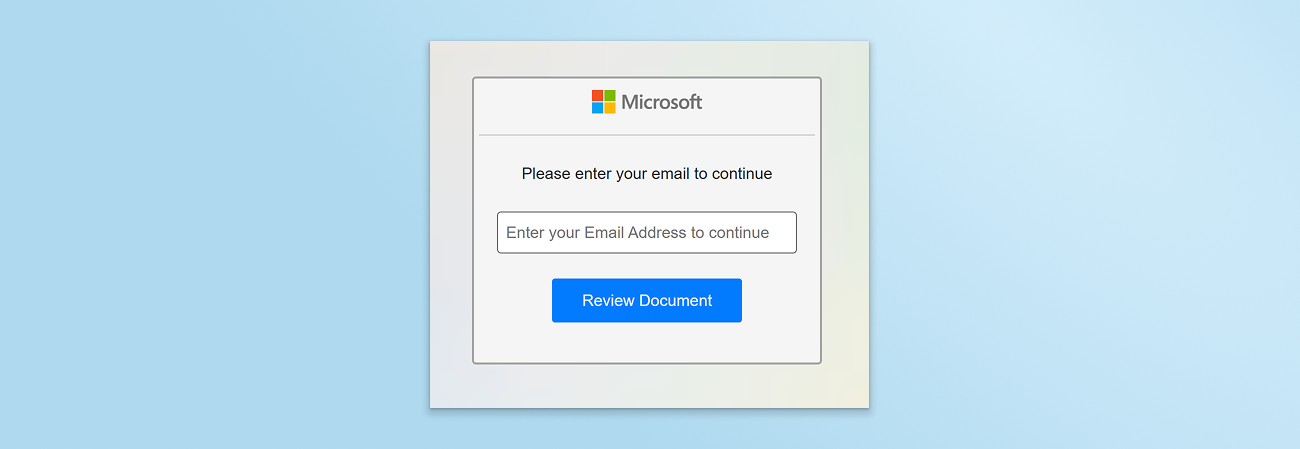
Bypassing Email Security, Firewalls, and SWGs
IT and security teams commonly implement a defense-in-depth strategy, layering controls so that an attack’s damage is mitigated, if not altogether prevented. In this case, the phishing attempt bypassed the first lines of defense—email filters, firewalls, and secure web gateways—and directly reached the user.
- The enterprise-level email platform didn’t flag the phishing email for any IOCs.
- The Monday.com form itself was hosted on a well-known SaaS platform.
- Network and web filters allowed traffic to all sites, all web pages.
If left undeterred, credential theft attempts that bypass upstream technical controls can easily fool users. Fortunately, the target organization’s browser security closed this otherwise critical gap.
Browser-Native Security Stops Credential Theft
Leveraging browsers’ vast visibility and innate capabilities to detect and respond to threats, browser-native security flagged the phishing attempt in real-time. By analyzing the content, behavior, and context of each page and user interaction, Keep Aware’s browser security solution recognized the suspicious credential request and paused the user before any data was entered, effectively stopping the compromise before it began.

Without this layer of in-browser protection, stolen credentials could have easily changed hands in the dark corners of the internet, sold on underground forums, and reused weeks or months later for unauthorized logins. With valid credentials, attackers often appear as legitimate users, leaving security teams with little visibility into how or when access was first gained, if they notice at all.
This is why browser-native security is essential: it operates at the point of interaction, detecting and interrupting malicious behavior as it happens.
SaaS Abuse and the Rise of ChainLink Phishing
This campaign is part of a growing trend we call ChainLink Phishing, attacks that chain together legitimate web services and compromised sites into one seamless chain of links to evade detection and steal credentials.
Monday WorkForms is just the latest example. We’ve also seen attackers abuse platforms like Google Drawings, Confluence, Dropbox, OneDrive, Scribe, and other trusted SaaS tools to host intermediary pages between email and phishing forms. These platforms are easy to weaponize and nearly impossible to block outright without disrupting legitimate business use.
To learn more about how these multi-stage phishing chains work—and how browser-native security interrupts them—watch our ChainLink Phishing webinar.
Indicators of Compromise (IOCs)
noreply@daysmart[.]com — Sender email addresshttps[:]//pub-0e49e11786394546a001eb1744600acd[.]r2[.]dev/newscandocument[.]html — Phishing pagehttps[:]//forms[.]monday[.]com/forms/19a6056cbc42eb875159805d16df247f — Intermediary phishing page





