
New ConsentFix Attacks Abuse Legitimate OAuth Flows
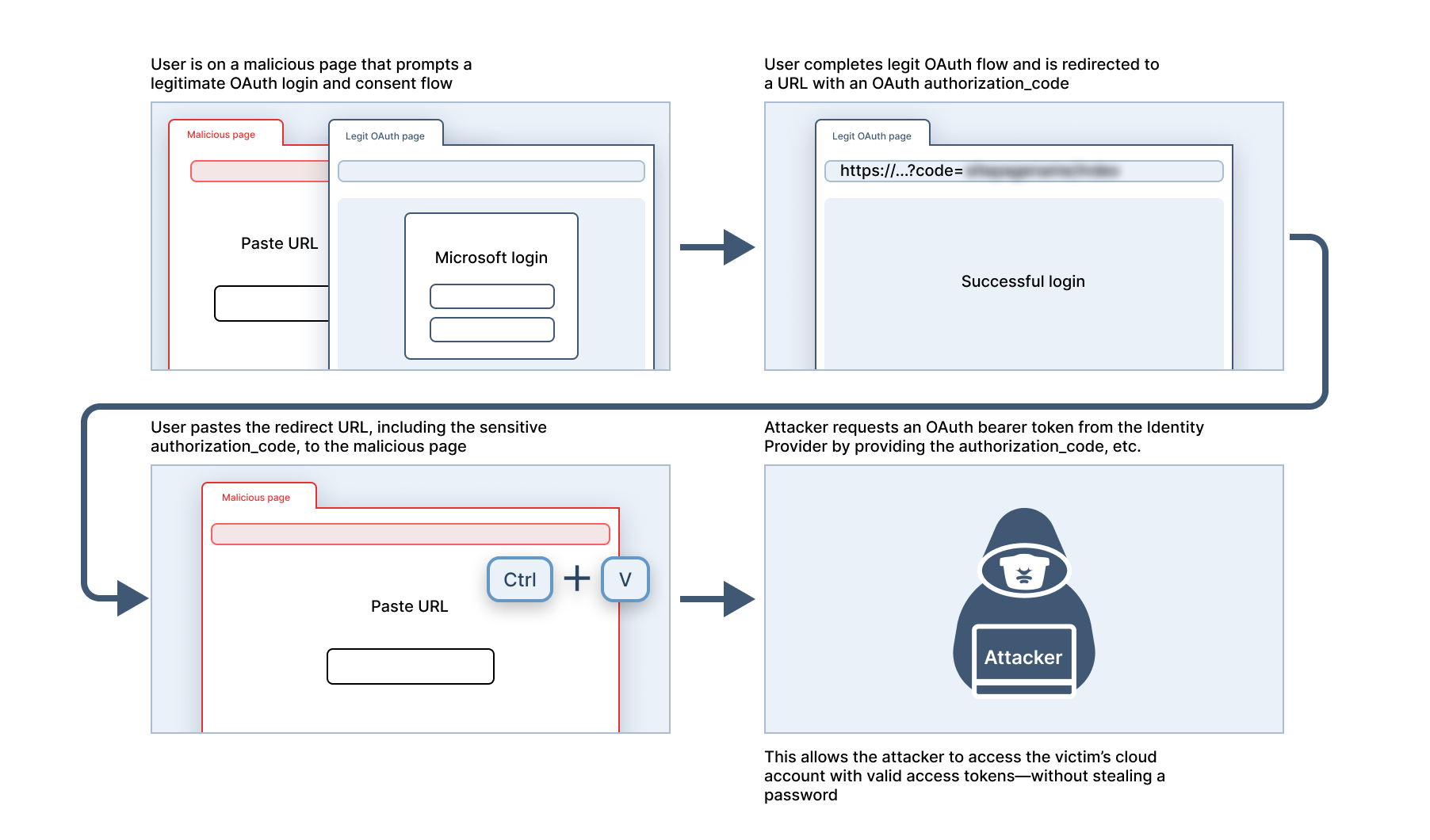
ConsentFix is a newly observed browser-based phishing technique. Named based on its purported predecessor, ClickFix, ConsentFix has similar social engineering prompts to ClickFix attacks. However, where ClickFix requires a user to paste malicious commands to compromise the host device, ConsentFix tricks a user into pasting an OAuth authorization code to an attacker-controlled site, thereby compromising the victim’s cloud account.
Example ConsentFix Attack Scenario, Compromised Microsoft Account
- A user is prompted by an attacker-controlled web page to authenticate their Microsoft account via a legitimate Microsoft sign-in URL.
- After authenticating, the sign-in flow legitimately redirects the user to a URL containing an authorization code tied to the user’s account.
- The user then copies and pastes the URL into the malicious web page, per its instructions.
- With the OAuth authorization code tied to the victim’s account, the attacker can now gather access tokens, gaining access to and compromising the victim’s Microsoft account.
Traditional Controls Miss ConsentFix, A Browser-Based Phishing Attack
Traditional security defenses are likely to miss this malicious activity because ConsentFix abuses legitimate OAuth authentication and consent flows that occur within the browser.
MFA is successfully bypassed without hindrance. The endpoint doesn’t see phishing page prompts. And email security is completely avoided when the attack originates through a malvertisement, SEO poisoning, or a compromised website.
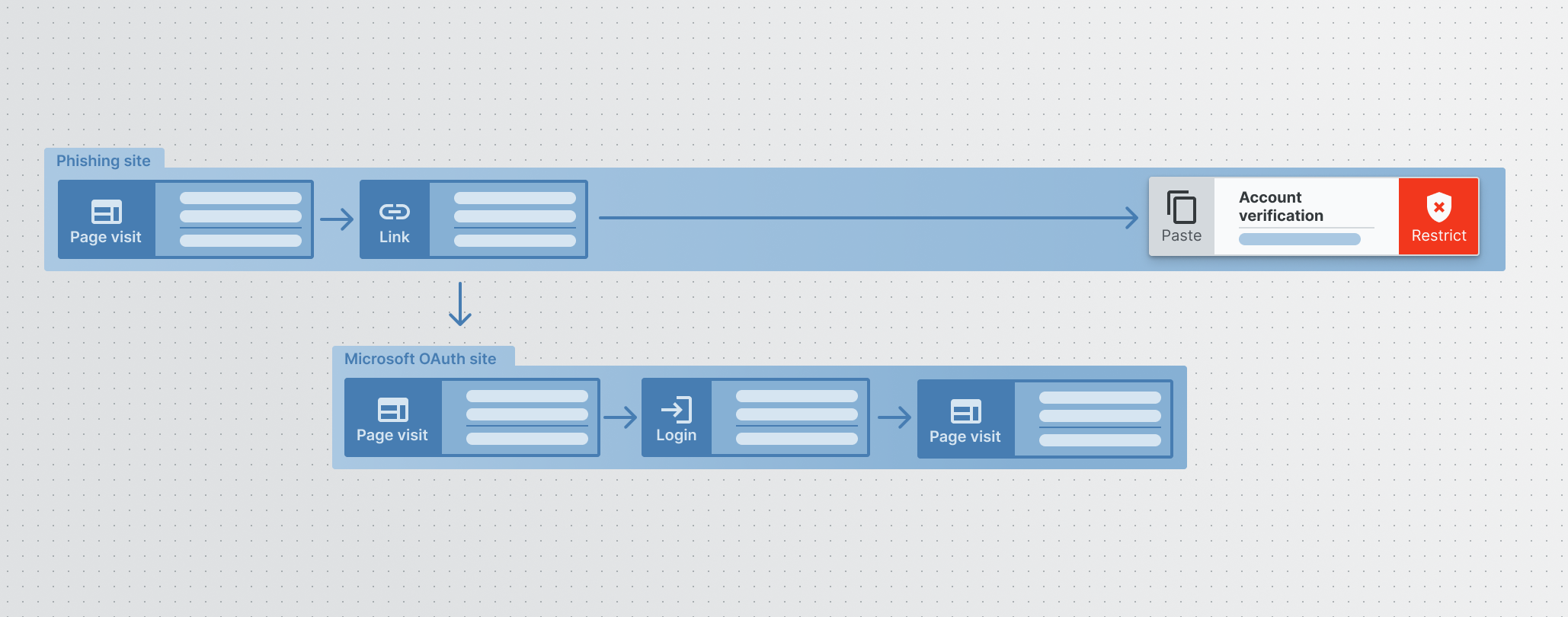
How BDR Detects ConsentFix in Practice
Browser detection and response (BDR) tools can provide valuable insight into what is actually happening in users’ browsers.
By empowering organizations with visibility into user activities in the browser and the ability to investigate browser sequences, and not just single events in time, BDR solutions are uniquely positioned to detect and prevent browser-based attacks.
Keep Aware specifically empowers security teams to defend against phishing attacks like ConsentFix by identifying suspicious user activity in the browser and flagging OAuth URLs pasted into untrusted sites.
What Security Teams Should Do for ConsentFix
A strong security defense against phishing attacks includes educating end users on how to spot them. Specifically for ConsentFix, encourage users to avoid pasting any authentication or other sensitive URLs into suspicious and untrusted sites.
Keep Aware strongly recommends reviewing browser telemetry and BDR alerts for suspicious consent and authentication activity and treating browser visibility as a high-quality signal in identity defense. Because ConsentFix is a reminder that modern phishing attacks happen where users work—inside the browser.



