Recently, one of our customers encountered a ChainLink phishing campaign—a multi-stage attack that guides the user through multiple links before reaching the final phishing site. This campaign, designed to steal Microsoft credentials, leveraged a trusted platform (GitHub Pages), a redirection chain, and a CAPTCHA.
Without real-time protection, this attack could have easily tricked the user into handing over sensitive login details. Here’s how the attack unfolded:
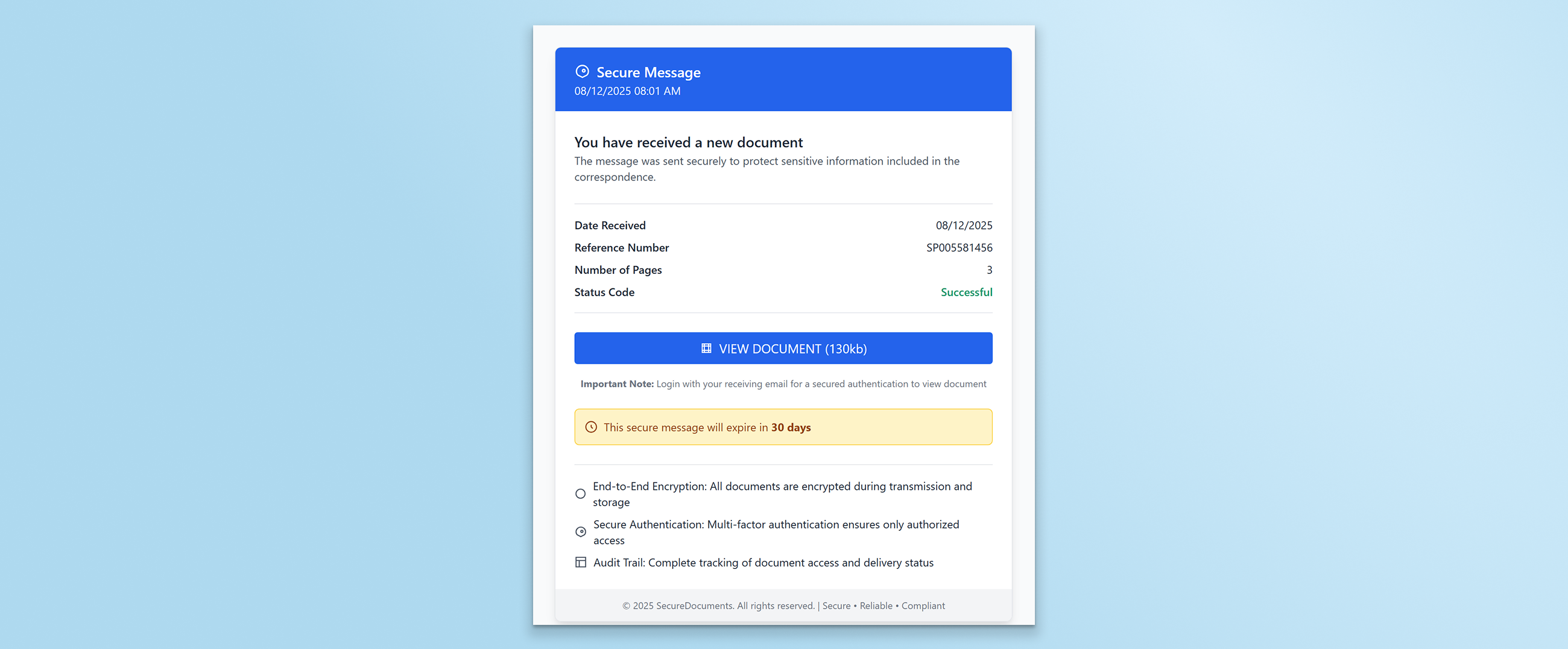
Step 1: Email to “Secure Message” GitHub Page
After clicking a phishing email link, the user ended up on a GitHub-hosted page titled “Secure Document Delivery”.
The page posed as a professional file-sharing portal, complete with claims of “end-to-end encryption”, “secure multi-factor authentication”, and “complete audit trails.” It instructed the user that they must log in with their receiving email account to access the document. A hyperlinked button labeled “VIEW DOCUMENT (130kb)” lured the user to the next stage.
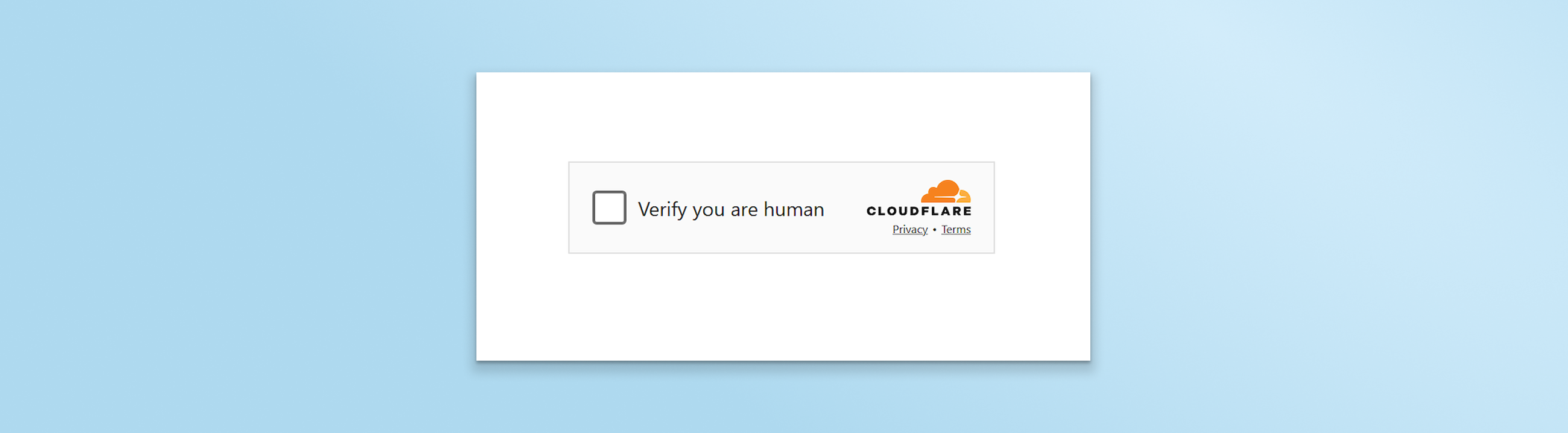
Step 2: Redirects and CAPTCHA
Clicking the link pushed the user’s browser to a young and risky site, keepviewprofile[.]pioneercircle[.]de, then to a link redirector service, href[.]li, and lastly routed to the final phishing domain.
The phishing site first displayed a CAPTCHA before rendering the phishing content.
Step 3: Microsoft Phishing (Blocked in Real Time)
After completing a legitimate Cloudflare CAPTCHA prompt, the final stop was a Microsoft credential phishing page hosted on a codezilla[.]online subdomain. The Keep Aware browser extension immediately recognized it as Microsoft phishing and halted the user from proceeding.
Importantly, during later out-of-band research, this phishing page no longer rendered—the infrastructure had already been taken down, only days after the attack. Without Keep Aware’s inline, real-time detection and logs, a security team would be left blind:
- The user may have believed the login page was legitimate.
- Credentials could have been stolen, leaving corporate accounts exposed to unauthorized access.
- After credential theft, there would be no digital evidence of the theft or of the phishing page content.
.png)
Why Real-Time Detection Matters
This incident highlights the critical value of inline response and real-time protection, especially for multi-step phishing attacks:
- Stops compromise before it happens. The Keep Aware extension prevented the user from ever entering business credentials.
- Gives visibility to the security team. Even when phishing infrastructure disappears quickly, detections and logs remain, ensuring defenders know what users encountered—and if credentials were handed over.
- Protects against ephemeral threats. Campaigns that vanish after a few hours or days are increasingly common. Reactive approaches simply can’t keep up.
Key Takeaway
ChainLink phishing campaigns are evolving to use ephemeral infrastructure, redirect chains, and trusted platforms like GitHub Pages to trick users and bypass traditional security controls. Security teams need real-time, inline, browser-capable defenses to protect employees at the moment of risk—before credentials are unknowingly stolen.
Our customer never reached the point of compromise because browser-native visibility and real-time detection stopped the attack in its tracks. Interested in seeing Keep Aware’s capabilities for yourself? Request a personalized demo with a team member to learn more.
IOCs
Domains
cjohnsongis[.]github[.]iokeepviewprofile[.]pioneercircle[.]dehref[.]li*[.]codezilla[.]online
URLs
cjohnsongis[.]github[.]io/Project-Documentation/keepviewprofile[.]pioneercircle[.]de/prk12/