Overview
A recent phishing attack exploited the trust security tools have in Zoom Docs, the collaborative workspace feature of Zoom, to host intermediary phishing pages designed to steal user credentials.
Phishing Email Allowed, Link Leads to Credential Theft
From a convincing email lure to a legitimate Zoom Docs link, the phishing attack began with a malicious email. The victim received an email prompting them to review a document (Subject: “You are invited to Review & Approve"). The email link led to a docs.zoom.us page, a legitimate domain, which displayed what appeared to be a DocuSign prompt inviting the user to “Review and Approve” a document.
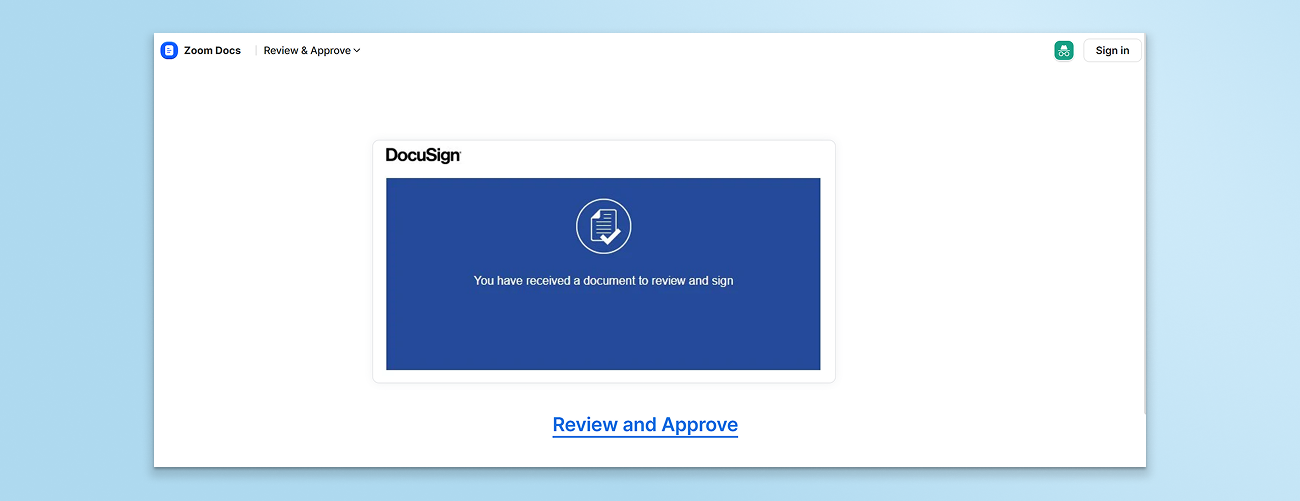
Upon clicking the DocuSign link, the user was redirected to a malicious site impersonating a Google login page, attempting to harvest the victim’s credentials.
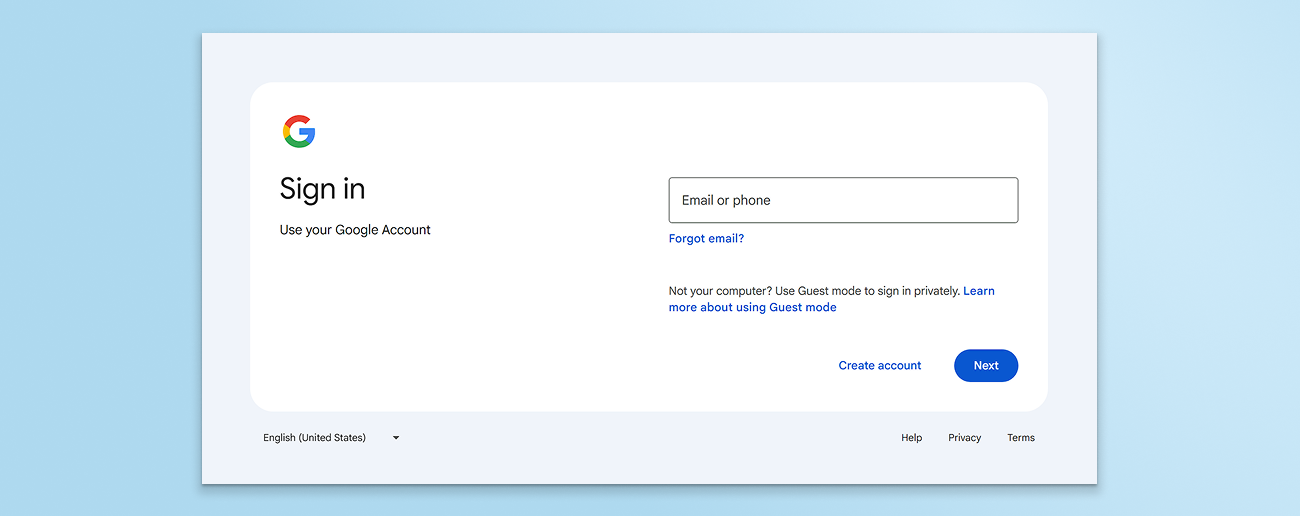
Keep Aware’s browser-native security detected and blocked the phishing attempt in real time, preventing credential theft. But this attempted attack underscores the reality of today’s threat landscape: Attackers don’t need savvy zero-days to evade detection and harvest user credentials, they simply impersonate trusted brands and use trusted web applications.
Zoom Docs is One of Many Legitimate Platforms Used for Effective Phishing
This is one of many examples of what we call ChainLink phishing, attacks that chain together legitimate websites to evade detection, reach the victim’s browser, and attempt credential theft. By leveraging trusted platforms like Zoom Docs, attackers can host malicious links without triggering traditional email or network-based defenses.
These intermediary pages are effective because they appear legitimate to both tools and users:
- The domain is reputable and trusted (docs.zoom.us).
- The content looks familiar (DocuSign branding).
- The call-to-action is expected for DocuSign actions (“Review and Approve”).
Traditional security layers—such as email security, network filters, and web gateways—see only legitimate domains and normal traffic. If the final phishing site is not blacklisted on the feeds your network tools subscribe to, then the malicious intent is only visible in the browser, where the final page renders.
Browser-Native Protection Stops Evasive Phishing
Keep Aware’s browser-native security solution monitors browser activity in real time, analyzing rendered pages and behavioral cues to detect phishing and credential-harvesting attempts, even when they abuse trusted infrastructure.
In this case, Keep Aware recognized the deceptive attack, blocked the final phishing page, and safeguarded the user’s credentials. The browser is where trust is tested and verified. As attackers continue abusing legitimate SaaS platforms, browser-native visibility becomes critical for stopping phishing chains before valid credentials are silently stolen.
Want to learn more about ChainLink phishing attacks? See phishing walkthroughs, the many legitimate platforms—and compromised domains—attackers are actively abusing, and what your security team can do to prevent these evasive, chained attacks by watching our ChainLink Phishing on-demand webinar.