
Imagine getting an email with a link to “accounts[.]ɢoogle[.]com”. At a glance, it looks legitimate—but that domain isn’t what it seems. The “ɢ” isn’t the familiar Latin character, “G”. The link may be a homoglyph (or homograph) domain attack, where cybercriminals register lookalike domains using characters from different scripts to impersonate trusted brands.
These domain attacks are designed to fool users, but they don’t fool browsers—or our security browser extension.
Homoglyph Domains and Punycode Encoding
When you type "accounts.google.com" into your browser, it sees exactly that: a domain composed of standard ASCII characters. But internationalized domains, those using non-ASCII characters, are encoded using something called Punycode. This is how browsers translate characters like non-standard English Latin, Cyrillic, Greek, or Japanese symbols into an ASCII-compatible format, which is required for DNS.
So, “accounts[.]ɢoogle[.]com” (with a Latin small capital "G") becomes “accounts[.]xn--oogle-wmc[.]com” (ASCII-compatible Punycode domain).
.png)
The “xn--” prefix tells the browser and DNS that the domain includes non-ASCII characters. Most modern browsers display these Punycode-encoded domains. That way, users can spot the odd encoding and steer clear of potential threats.
But what happens when they don’t?
A New Twist: When Browsers Don’t Show the Encoding
A recent phishing campaign exploited a Japanese character, "ん", to create domains that look like file paths, such as:
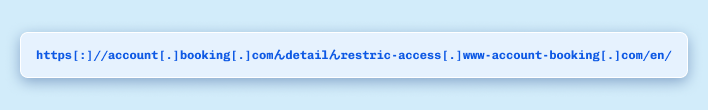
The twist? Browsers like Chrome display this domain in the address bar as-is—no Punycode shown. In the hands of attackers, it’s a perfect lookalike for legitimate domains.
The outcome: users struggle to quickly differentiate between the real domain and the deceptive file path, which creates a prime opportunity for phishing and credential theft. Luckily, browser security solutions are designed to catch these attacks.
How Keep Aware Protects You
Our browser security extension is designed to catch what users may miss. Even if a browser chooses not to display the Punycode version of a domain, Keep Aware analyzes the underlying domain string in real-time.
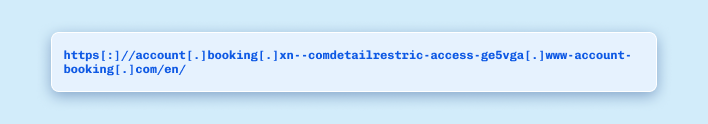
Whether an attacker swaps in the obscure Latin letter “ɢ” or the Japanese character “ん,” our solution spots the potential deception, even when it’s invisible to the user.
Why It Matters
Homoglyph attacks are subtle but powerful phishing tools. They're difficult to detect with the human eye and can be used to host near-perfect clones of popular login portals or support pages, leading to credential theft and credible-looking social engineering attacks.
Stay Aware, Stay Protected
Phishing attacks are here to stay. Relying on email filters, web security, and human discernment has proven to be an ineffective security strategy against corporate credential theft. Phishing detection must happen at the point of click—past traditional perimeter controls and underneath what the user sees.
If you want to see how Keep Aware can protect against a homoglyph domain attack in real-time, feel free to schedule a personalized demo with a team member.




